Technology teams face constant change. New tools and workflows appear every year, and the pace has only accelerated with containers and cloud-native architectures. These shifts reshaped how software is built and managed. Two of the biggest shifts have been DevOps and, more recently, DevSecOps.
DevOps changed how software gets built by bringing development and operations together. The goal was straightforward: ship faster and adapt quickly. It worked—but it left one big gap: software security.
Security couldn’t afford to lag. It had to evolve from a reactive checkpoint to a proactive part of the software development process.
That’s where DevSecOps steps in—embedding security into every phase of the software development cycle.
Here’s what you need to know about DevSecOps and its role in your organization’s ROI.
What is DevSecOps?
At its core, DevSecOps brings security into the same workflows that development and operations teams already use. Instead of slowing things down with legacy checks at the end, security moves upstream, reducing delays and catching issues before they become expensive problems.
The result is a culture where accountability and security are based on shared responsibility. Security considerations become part of daily workflows rather than barriers at the end of the process. With this shift, businesses can accelerate software development without increasing risk exposure.
Adopting DevSecOps for your business means:
• Considering production environment and infrastructure security from the beginning of the development lifecycle.
• Automating security tasks and gates to keep up with the DevOps pace.
• Picking the right tools to ensure the continuous integration of security.
• Adopting cultural changes across the organization to integrate the security team.
Security Teams in DevOps Vs. DevSecOps
Some may argue that DevOps already includes security elements. In practice, however, security in traditional DevOps often functions as an external layer rather than an embedded principle. Vulnerabilities are typically caught late, when fixes are more costly and disruptive.
In contrast, DevSecOps embeds security into the pipeline itself. As a result, security vulnerabilities can be identified early. Security professionals start acting as enablers—defining acceptable risk thresholds and ensuring the process remains both fast and compliant.
DevSecOps Components
A working DevSecOps model depends on a few essentials: ongoing code reviews, smart change management, continuous compliance, security threat modelling, and regular training to keep development and operations teams sharp.
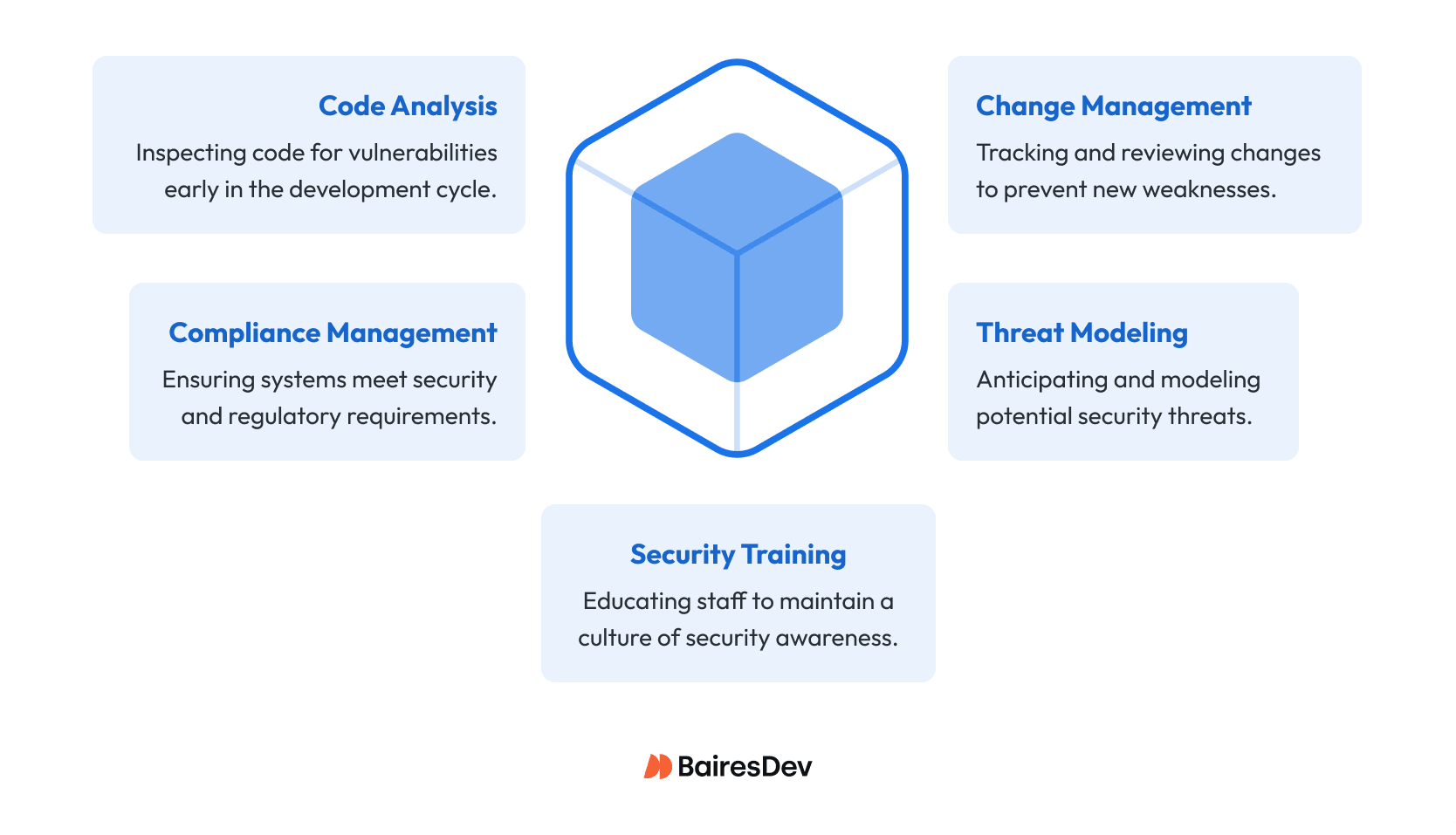
Code Analysis: Teams inspect source code for vulnerabilities. Breaking work into smaller pieces makes it easier to spot issues early and fix them before they spread further into the pipeline.
Change Management: Every change needs tracking and review. Effective processes log updates, assess security risks, and reduce the chance of introducing new weaknesses.
Compliance Management: Regulations don’t wait for release schedules. Continuous auditing ensures that systems meet security and regulatory requirements at every stage, avoiding costly surprises later.
Threat Modeling: Anticipating risks is as important as fixing them. By modeling potential security threats before and after deployment, software developers strengthen defenses and close gaps faster.
Security Training: People are part of the system. Regular training keeps developers and operations staff current with the latest practices, building a culture of security awareness.
Benefits of DevSecOps and Automated Security Testing
Automating security testing is central to DevSecOps. By embedding automated checks into the pipeline, teams catch vulnerabilities early, when fixes are faster and cheaper. Real-time feedback lets developers address issues as they code, preventing security from becoming a release blocker.
This continuous, proactive approach reduces risk exposure, strengthens compliance, and improves software quality without slowing delivery. It also minimizes manual effort, freeing teams to focus on high-value work. For CTOs balancing speed and resilience, such security testing is the mechanism that makes security a routine part of the lifecycle—not an afterthought.
Security Testing
This comprehensive approach includes dynamic application security testing (DAST), static application security testing (SAST), and interactive application security testing (IAST).
Dynamic Application Security Testing (DAST): DAST involves testing the application while it is running. This type of testing simulates real-world attacks to identify vulnerabilities that could be exploited by malicious actors.
Static Application Security Testing (SAST): SAST involves analyzing the source code for vulnerabilities. This type of testing is performed early in the development process, allowing developers to identify and fix security flaws before the application is deployed. SAST helps ensure that the code is secure from the outset, reducing the risk of security breaches.
Interactive Application Security Testing (IAST): IAST combines the benefits of DAST and SAST to provide comprehensive security testing. By analyzing both the running application and its source code, IAST offers a holistic view of the application’s security posture. This integrated approach helps identify and address security issues more effectively.
How to Get Started with DevSecOps in the Software Development Lifecycle
A significant cultural shift is the best starting point for implementing DevSecOps: reassessing the role of the security team in the pipeline. This means reassessment of the role of the security team in the pipeline.
Security can’t be treated as a nuisance or something to trade away for speed. The development and operations teams that succeed are the ones that view it as a built-in safeguard against costly problems later.
Of course, it’s more than mindset. You also need to adjust operational processes.
DevSecOps has several components you should tackle at the beginning to ensure its proper adoption.
- Code analysis: The development team has to deliver small pieces of code to let the security pros assess them in search of vulnerabilities. The size of those chunks is important, as being small will allow the security team to find issues more quickly.
- Continuous auditing: The security team should always be on the lookout for compliance with both security requirements and applicable regulations. You should conduct regular security controls to make sure that everything is in the right place.
- Change management: You should make it easy for teams to submit changes to increase the speed at which you apply them. Naturally, before doing so, you should define if the change is good enough to be applicable.
- Continuous threat monitoring: Every time the team updates the code, new potential threats can emerge. That’s why you should check each and every update and address any emerging security issues quickly to prevent further consequences.
- Performance assessment: Measure how quickly the team responds to new vulnerabilities. Consider measuring the time it takes for them to identify new vulnerabilities and patch them.
- Constant training: Security practices in DevSecOps have to be constantly updated, which means that your team has to keep up with the latest as well. Be sure to provide them with continuous training to ensure the necessary level of security for today’s standards.
- Software composition analysis: Automate the visibility into the use of open-source software to manage risks, ensure security, and maintain license compliance.
The Time for DevSecOps is Now
Leaders today need to deliver faster and more secure software without putting the business at risk. DevSecOps provides that balance—keeping the speed of DevOps while ensuring security measures and compliance are part of the build, not an afterthought.
At BairesDev, we’ve already adopted this approach into our delivery processes to help clients meet the demands of today’s market.






