Lacking a SOC 2 report can quietly kill your enterprise deals, long before a buyer ever says “no.”
Procurement teams bound by regulatory oversight often stop the process the moment they see a gap. Your product might be best-in-class, but without proof of dependable systems, it won’t get past the vendor review.
For engineering leaders, SOC 2 compliance should never be treated as a paperwork task. It’s how service organizations prove to business partners, customers, and regulators that internal controls and robust security measures are in place. The payoff is practical: shorter sales cycles, fewer questionnaires, and fewer chaotic incidents when something goes wrong.
“Without SOC 2, deals stall. With it, you prove dependability, cut weeks from procurement, and reduce the blast radius of incidents.”
SOC 2, done right, is not an audit exercise. It’s an accelerator for delivery, trust, and growth.
Why SOC 2 Matters to Your Organization
SOC 2 is not just a checkbox. Procurement teams explicitly call for SOC reports in vendor oversight. If you can’t produce one, your product may never make it past due diligence.
With a current SOC 2 Type II report, you provide an objective assessment from external auditors that your systems meet the Trust Services Criteria. Instead of spending weeks answering bespoke questionnaires, you offer a single attestation prepared by certified public accountants following the American Institute of CPAs (AICPA) SOC 2 standards.
The benefits ripple across your team. Strong security controls prevent credential misuse. CI/CD gates improve operational effectiveness. Centralized logs and tested incident plans reduce downtime and limit the impact of cyber threats. In industries where the average data breach costs $4.88M globally, compliance safeguards both your roadmap and your brand reputation.
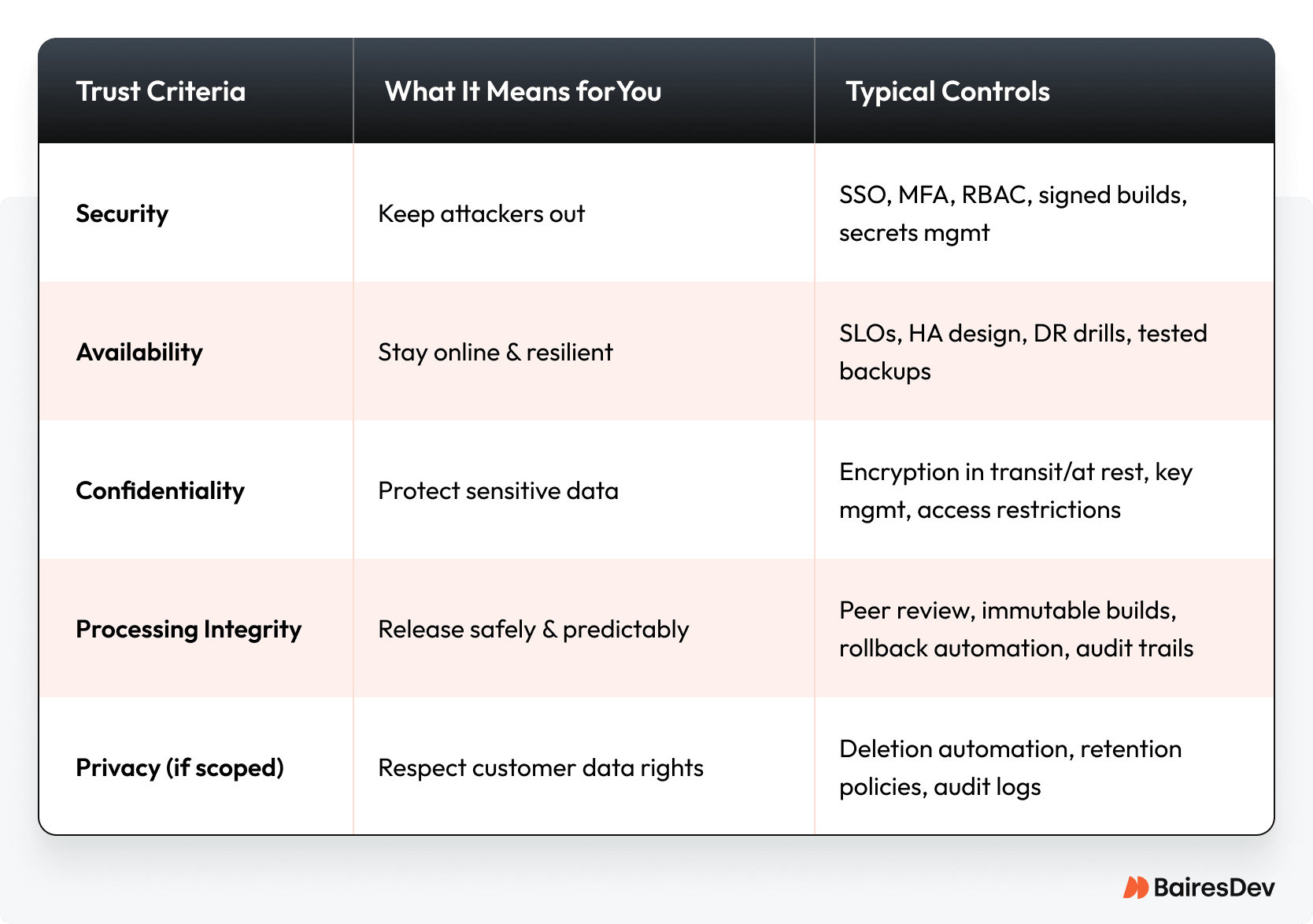
How the Trust Criteria Map to Your Systems
SOC 2 rests on five Trust Services Criteria. Each one ties directly to your systems and processes:
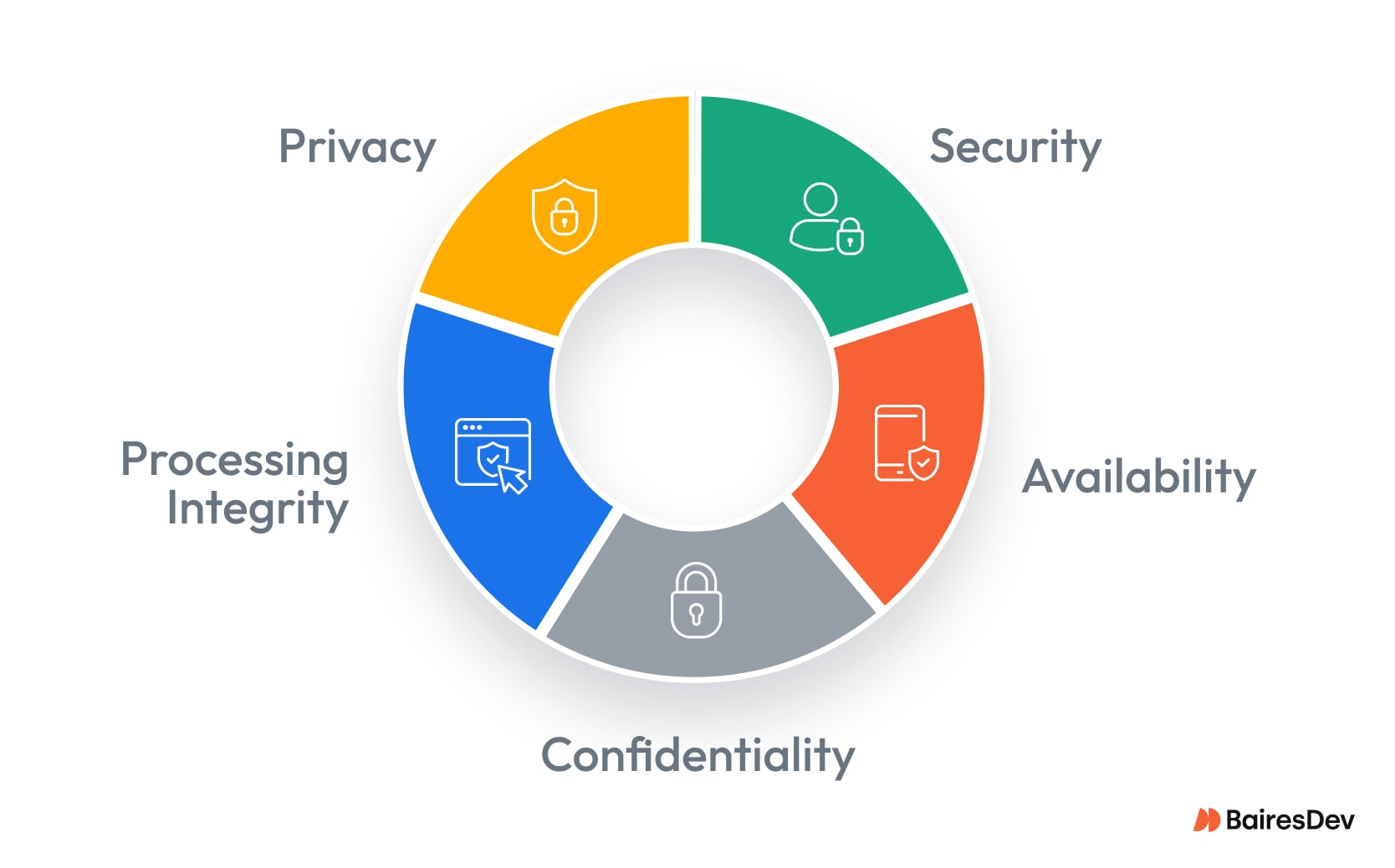
- Security: Protect systems against unauthorized access with SSO, multi-factor authentication, RBAC, and signed builds.
- Availability: Prove uptime with SLOs, tested backups, and disaster recovery drills.
- Confidentiality: Encrypt data in transit and at rest, restrict keys, and limit privileged roles.
- Processing Integrity: Ensure reliable data processing through peer review, automated testing, and rollback plans.
- Privacy (when in scope): Respect privacy principles with retention and deletion automation, particularly for customer data.
These are not abstract requirements. They’re controls that directly support information security and reinforce delivery discipline.
Trust Criteria → Systems (quick map)
Your Compliance Is Only as Strong as Your Vendors
SOC 2 doesn’t stop at your own systems. It extends to the service providers and partners you depend on. Cloud services, analytics platforms, and contractors can all become weak links. If they fail, your security posture weakens with them.
That’s why part of readiness is vendor management: keeping an inventory of providers, reviewing their SOC reports, and enforcing compliance obligations. Enterprise buyers expect entities to hold their vendors to the same compliance frameworks. Architecturally, this means designing with supply-chain risk in mind and ensuring your organization controls are enforceable end-to-end.
The Business Impact You Can Expect
SOC 2 delivers benefits in three areas:
- Deal velocity. Enterprise buyers, bound by regulatory compliance rules, review SOC 2 reports before approving contracts. With a valid Type II report, procurement cycles shrink from months to weeks.
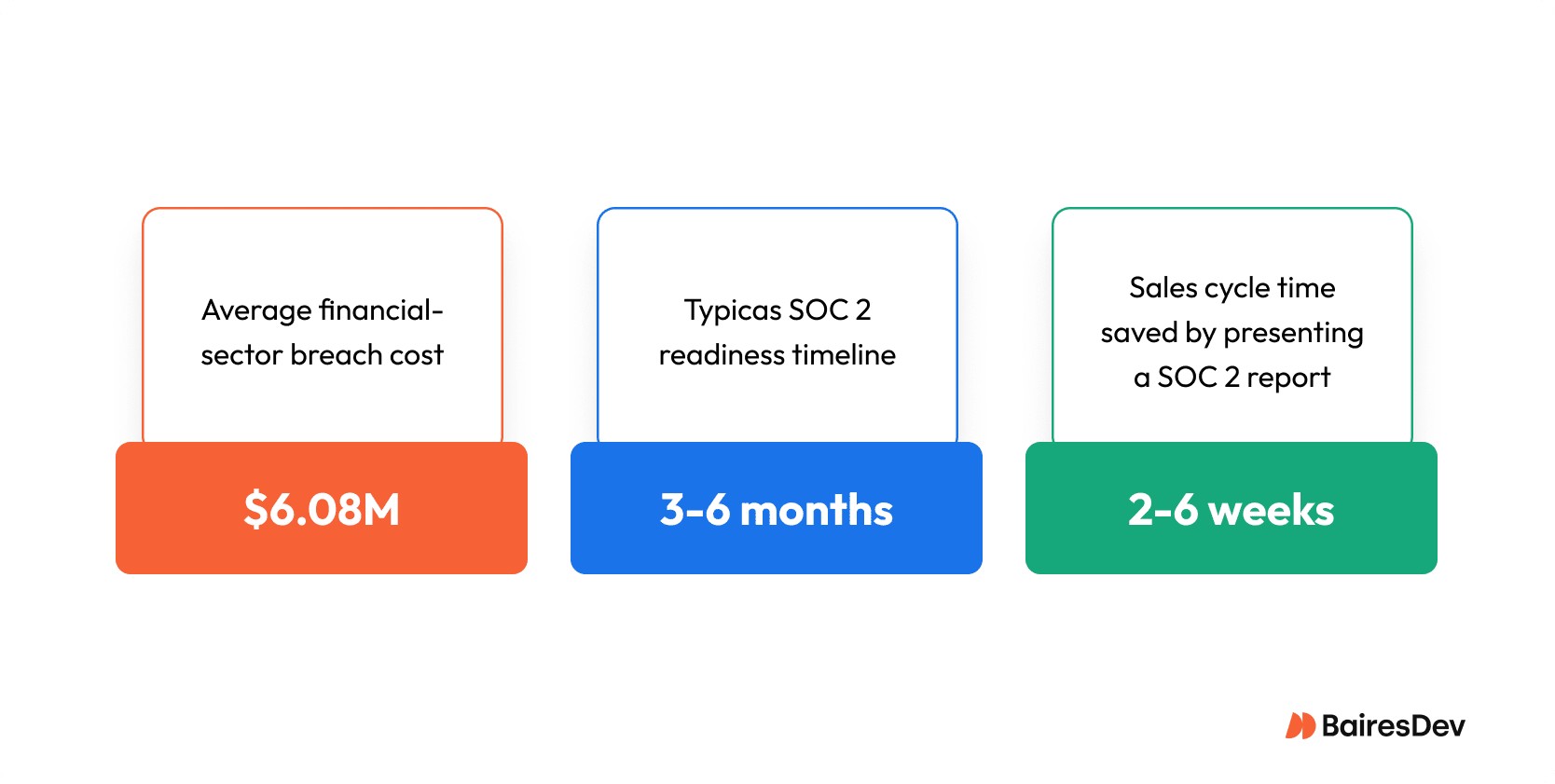
- Risk management. SOC 2 reduces the likelihood and impact of data breaches. The global average breach cost is $4.88M, and in financial services it exceeds $6M. Controls around access, logs, and incidents are levers against those losses.
- Operational maturity. Practices that auditors test—peer review, immutable logging, encryption—also improve uptime and MTTR. That means fewer failed changes and less chaos.
The result is a clear competitive advantage: less time wasted on questionnaires, more time invested into features.
What “Good” Looks Like in Practice
When SOC 2 is embedded, it feels like engineering hygiene, not compliance overhead.
- All accounts use SSO and multi-factor authentication.
- Privileged roles are temporary, logged, and reviewed quarterly.
- Pipelines enforce scans, signed builds, and peer reviews.
- Infra is deployed from immutable images under version control.
- Logs are centralized and immutable for accountability.
- Sensitive information is encrypted, keys are segregated and rotated.
- Sensitive customer data is deleted per retention policies.
- Incident response is drilled, and playbooks rehearsed.
These are not just audit items. They’re security measures that protect customer data and keep delivery velocity high.
SOC 2 Compliance Myths and Misconceptions
Let’s address some common misconceptions and myths related to SOC 2 compliance:
- “SOC 2 slows delivery.”
In reality, it shifts effort from reactive firefighting to proactive discipline. By embedding automated security and quality gates into the pipeline, SOC 2 eliminates the manual reviews and emergency fixes that are the true killers of development velocity. - “SOC 2 is only for FinTech.”
SOC 2 has evolved into the universal standard for B2B trust. Any enterprise will expect it. Procurement and security teams in virtually every industry now consider it a baseline requirement for vendor approval. - “SOC 2 is a one-time project.”
The audit is a point-in-time validation, but compliance is continuous. Its true value lies in embedding security controls into daily operations to demonstrate ongoing operational excellence and a commitment to customer trust.
Implementation Realities You Should Expect
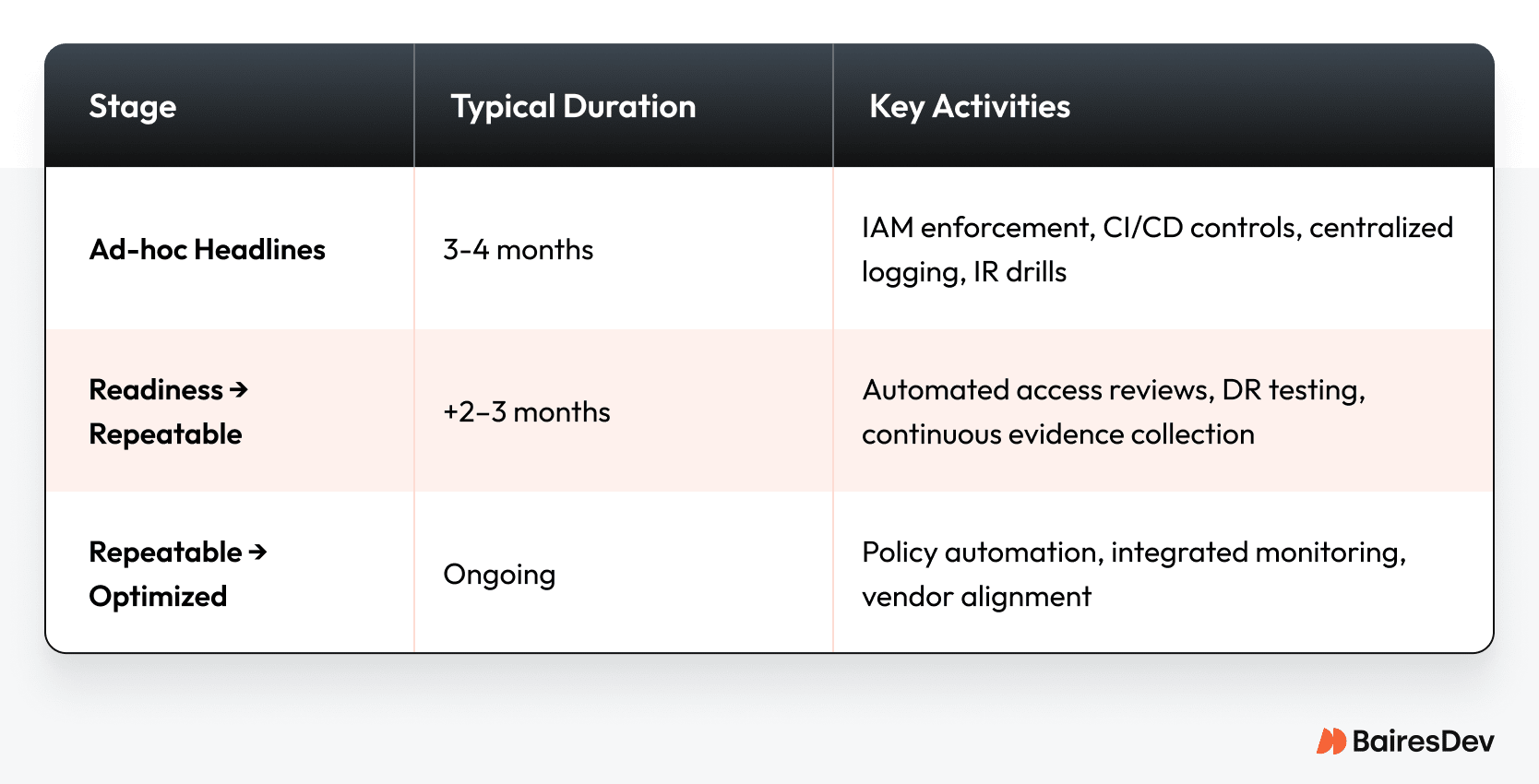
Reaching SOC 2 readiness in a reasonable timeframe is achievable, but it takes focus.
If you’re starting from an ad-hoc baseline, plan for three to four months of concentrated work. Getting to a repeatable, automated program often adds another quarter.
Costs break into three areas: auditor fees, tooling, and engineering time. Auditors typically fall in the low six figures. Smaller teams or startups may pay much less. Tooling investments include logging platforms, compliance automation, and backup systems. The largest cost is your team’s time—formalizing practices and producing evidence.
SOC 2 Type I vs. Type II: What Your Buyers Expect
- SOC 2 Type I shows controls are designed appropriately at a point in time. It’s a common first milestone and can satisfy early-stage stakeholders.
- SOC 2 Type II proves those controls operated effectively over a period (often 6–12 months). This is what most enterprise buyers look for in procurement.
Plan beyond the first audit. Type I buys you time, but Type II is where commercial credibility really begins.
Mini-Case: From Questionnaires to Closed Deals
One SaaS vendor faced endless questionnaires, pulling engineers off roadmap work for weeks. Deals stalled as procurement dug into security practices.
After earning a Type II report, certified by a third-party auditor, the outcome shifted. Reviews dropped from six weeks to under three. Customers trusted the objective assessment of controls. Deals closed faster, engineers focused on delivery, and the company protected both revenue and brand reputation.
The SOC 2 Readiness Checklist
Audit readiness means being able to demonstrate:
- Enforced SSO and MFA across accounts
- Privileged access reviewed quarterly
- CI/CD with peer review, scans, signed builds
- Infra as code with versioning and immutable images
- Centralized logging of authentication, changes, and incidents
- Tested backups with recovery objectives
- Drilled incident response with playbooks
- Encryption in transit and at rest
- Automated retention/deletion for private information
If you can show these controls, you’re close to audit-ready. More importantly, you are already demonstrating operational effectiveness.
BairesDev’s Perspective
At BairesDev, we see SOC 2 as more than audit readiness. We view it as a framework for scaling responsibly. The companies that succeed are those that embed security controls like access management, logging, and incident drills into daily work, not one-off audits.
That reflects how we operate: robust controls, transparent collaboration, and disciplined pipelines across distributed teams. For our clients, SOC 2 is a way to ensure security, protect sensitive information, and accelerate delivery without compromising trust.
Strategic Takeaways
- SOC 2 is not just a certificate—it’s assurance of information security and risk management.
- It helps you safeguard sensitive information, protect financial data and client data, and maintain customer satisfaction.
- It helps demonstrate alignment with security and privacy requirements in regulated sectors like healthcare and financial services.
- SOC 2 is how you convert trust into growth.
Trust as an Engineering Deliverable
SOC 2 proves your organization’s controls are real and enforced. It validates to user entities that your service organization can protect sensitive customer data and operate with resilience.
Compliance and delivery aren’t trade-offs. They can and must reinforce each other. The same controls that pass an audit also protect against cyber threats, enhance data security, reduce rework, and shorten recovery.
Trust has become an engineering deliverable. SOC 2 is how you show it.
Frequently Asked Questions
How to pitch SOC 2 to the board?
Position it as a two-for-one investment. It’s the seatbelt that protects the company from a multi-million dollar breach and the express lane pass that gets sales teams through enterprise procurement. The conversation must be framed around risk mitigation and revenue acceleration, not just compliance.
How to justify the budget?
Compare the fixed, known cost of a SOC 2 program to the unpredictable—and potentially catastrophic—cost of a lost enterprise deal or a public data breach. It’s a straightforward financial trade-off between a smart investment and a massive liability.
How to measure the ROI?
The ROI isn’t on a single dashboard. It’s visible in shrinking sales cycles and the hours reclaimed from filling out security questionnaires. It’s found in engineering stability and the reduction of reactive fire drills. The true return is organizational speed.
How long does it take?
Expect a 3-to-4-month project for Type I readiness. The Type II report, which is the one buyers value most, requires a subsequent 6-to-12-month observation period. This timeline is what gives the report its credibility; there are no shortcuts.
SOC 2 or ISO 27001?
This is about speaking the native language of the target market. For U.S. enterprise customers, that language is SOC 2. While ISO 27001 is a respected global standard, SOC 2 has become the non-negotiable standard for the US market.
Does SOC 2 replace HIPAA?
These are entirely different tools for different jobs. SOC 2 is a broad framework to prove a system is secure. HIPAA is a narrow, legally-mandated set of rules for protecting U.S. patient data. Handling that specific type of data requires both.
Is GRC software actually required?
It’s not mandatory, but attempting to manage an audit with spreadsheets is a recipe for human error and wasted months. GRC platforms exist to automate the evidence collection, reduce risk, and make the audit process manageable.