Reliable digital plumbing rarely earns headlines, yet it decides whether a purchase order clears before the nightly cut-off or sits untouched until a new batch window opens. Electronic Data Interchange (EDI) is that plumbing. It moves structured business information between companies without a human pressing send.
Event streams, REST, and GraphQL now dominate integration chatter, but EDI still carries the bulk of invoices, shipment notices, inventory updates, and customs filings in global supply chains. Two factors keep it firmly in place.
- Highly-regulated sectors need deterministic data flows that auditors can verify. EDI’s rigid schemas, functional acknowledgments, and time-stamped logs make compliance measurable instead of aspirational.
- Network effects – once a critical mass of trading partners aligns on a standard, ripping it out causes more disruption than refining the system already in production. Modernization therefore focuses on upgraded, not replacing the core contract that EDI represents.
The takeaway is simple: EDI remains a non-negotiable layer of integration infrastructure. Ignoring it risks chargebacks, delayed cash cycles, and strained partner relationships. Understanding how it works is table stakes for anyone charged with digital operations or revenue continuity.
What Is EDI?
Electronic Data Interchange is the automated exchange of machine-readable business documents between computer systems that agree on a standard format and a secure transport.
In practice it looks like this: your ERP generates a purchase order, translation software maps internal field names to the X12 850 schema, the payload travels over AS2 with TLS encryption, and your supplier’s gateway converts the message into its own data model before auto-creating a sales order. No manual keying, no PDF attachments, no ambiguity.
Strict contracts govern every step. Syntax and semantics are negotiated long before production traffic flows. Each data element has an agreed-upon position, length, and validation rule. Transmission methods, security certificates, and service-level targets are documented in trading partner agreements. The result is a deterministic workflow with fewer surprises.
Before diving into mechanics, it helps to compare EDI with the approaches it replaced.
EDI versus Traditional Document Exchange
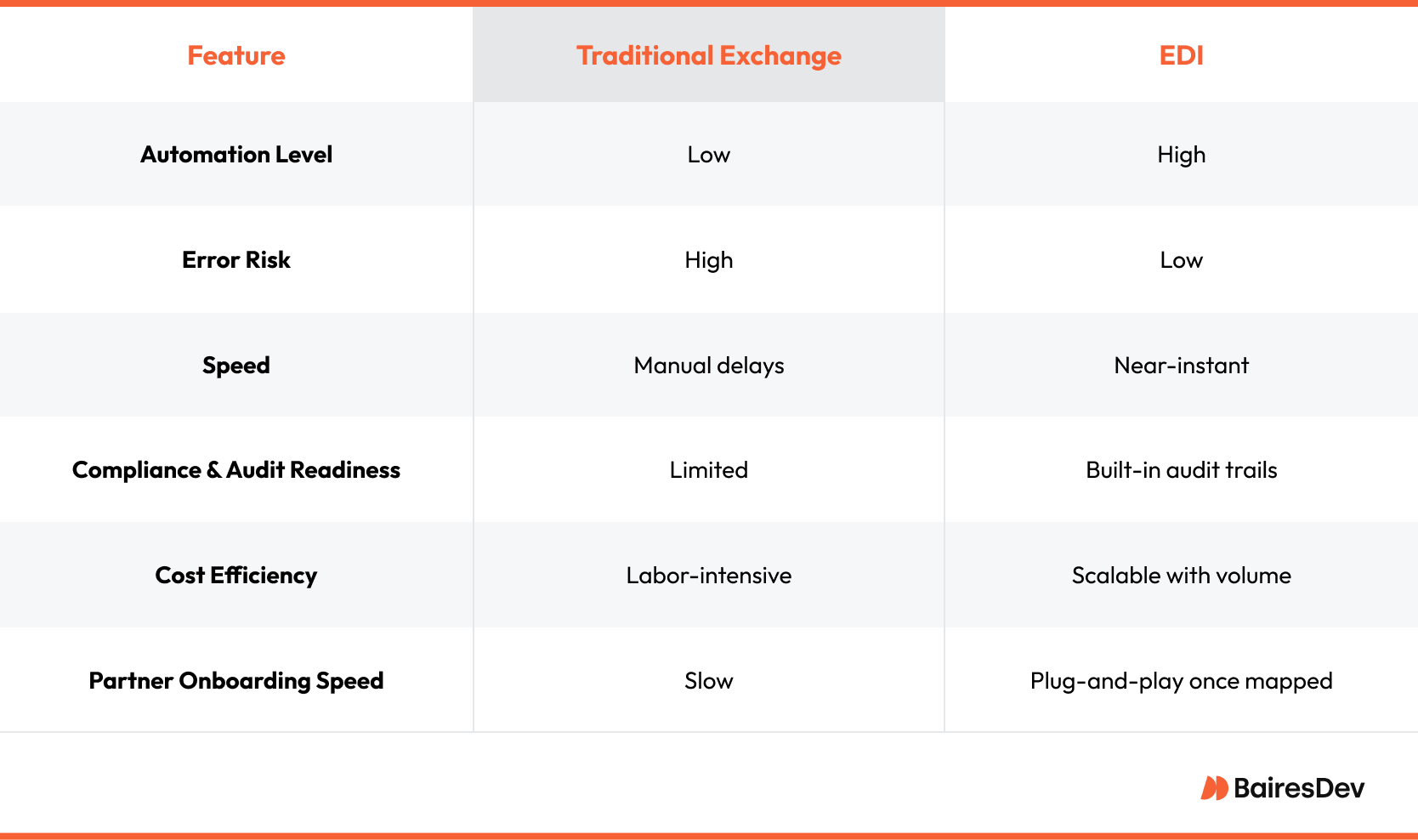
Legacy document exchange relies on people to bridge gaps. A buyer prints or exports a form, attaches it to an email, and hopes the supplier re-keys the content accurately. Even when encrypted email protects the transport, the payload remains an unstructured blob that someone must interpret.
EDI removes that uncertainty. Validation occurs automatically on both ends, and failures trigger functional acknowledgments that arrive in minutes. Error detection therefore moves to the front of the process rather than appearing as a costly downstream surprise.
Key Elements of an EDI System
A functional EDI stack contains four building blocks that work together:
- Standardized document sets such as X12 850 (purchase orders) or EDIFACT INVOIC (invoices).
- Mapping and translation logic that converts internal data structures to and from those standards while preserving data quality.
- Secure transport channels such as AS2, SFTP, or a value-added network that guarantee integrity, authenticity, and non-repudiation.
- Run-time controls for acknowledgments, exception handling, and audit trails demanded by regulators and customers alike.
With these components in place, structured data flows predictably between trading partners, and every transaction is traceable from origin to system of record.
EDI in Action: Business Documents and Other Use Cases
Conceptual clarity is helpful, but value becomes tangible only when mapped to daily operations. Most enterprises adopt EDI because a dominant customer demands it, then expand coverage once the return on investment becomes obvious.
Key Documents Transmitted via EDI
Transaction volume concentrates around a small group of messages. Purchase orders initiate demand and specify line-level quantities. Order acknowledgments confirm acceptance or propose changes. Advance ship notices provide carton-level detail before a truck leaves the dock, allowing warehouses to plan labor precisely.
Invoices trigger accounts-payable workflows, while remittance closes the loop when payment posts. Inventory reports, customs declarations, and transportation status updates round out the catalog, each with a reference number in the applicable standard that drives deterministic processing.
EDI Use Cases Across Industries
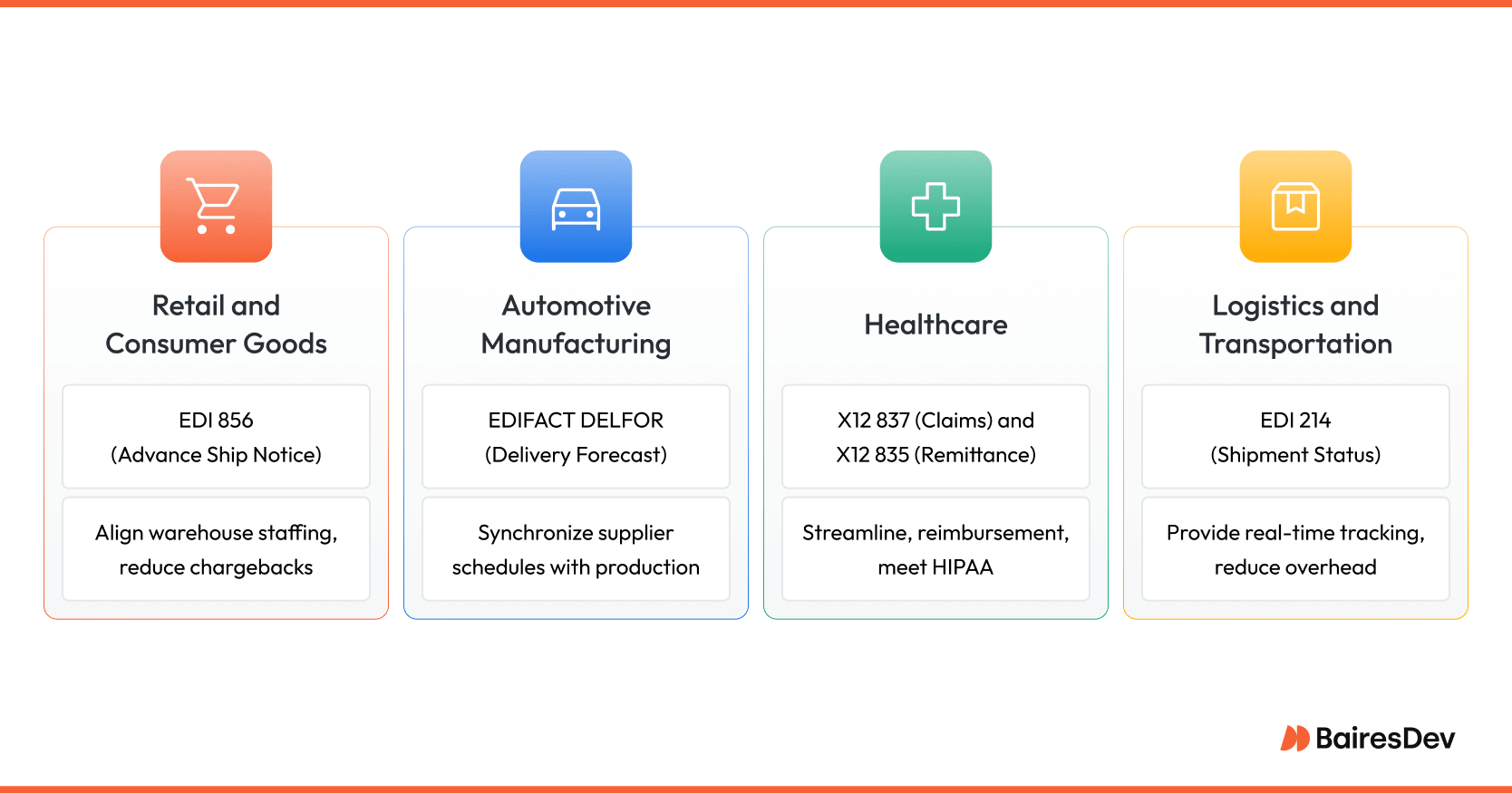
Retail and consumer goods
Large retailers impose strict delivery windows and chargebacks for lateness. EDI 856 advance ship notices feed warehouse-management systems so staffing matches inbound volume, eliminating dwell time at the dock.
Automotive manufacturing
Just-in-time production hinges on synchronized schedules. Tier-one suppliers send EDIFACT DELFOR call-offs aligned to takt time, preventing both line stoppage and excess inventory.
Healthcare
Hospitals and insurers exchange X12 837 claims and X12 835 remittance messages. The structured flow shortens reimbursement cycles while meeting HIPAA mandates for protected health information.
Logistics and transportation
Carriers push EDI 214 status updates that populate shipper portals with real-time milestone data, reducing track-and-trace calls and improving customer visibility.
Across these domains the pattern repeats: EDI codifies business rules, eliminates transcription errors, and gives leadership immediate insight into order lifecycles.
Behind the Scenes: How EDI Works in Enterprise Systems
A purchase order may look simple on a dashboard, yet a surprising number of moving parts carry it from one database to another. Understanding that invisible choreography helps leadership justify the line items that show up on an IT budget.
Every EDI exchange begins inside a source application, often an ERP or a warehouse-management system, that holds the “truth” about quantities, prices, or shipment dates. A lightweight export routine sends that data to a mapper. The mapper converts proprietary field names into the target document format, for example X12 850 or EDIFACT ORDERS. Think of it as translating idiomatic English into legal prose: the core idea stays intact but every comma finds its prescribed place.
Once mapped, the document is handed to the communications layer. Here you have options. A direct point-to-point link over AS2 keeps control inside your own perimeter. A value added network (VAN) shifts routing, retries, and mailbox management to an intermediary. SFTP, OFTP2, or even an IPsec tunnel may appear in legacy contracts, especially with automotive or government partners. What matters is that both sides agree on one secure protocol and keep certificates current.
Confirmation flows the other way. Functional acknowledgments let senders know whether the document passed basic checks. More granular application acknowledgments confirm that the receiving system actually consumed the data. These echoes feel bureaucratic until you lose a day’s revenue because an invoice never posted. They also feed operational dashboards that surface bottlenecks long before the quarter closes.
Step-by-Step View of an EDI Process
- Data extraction from internal systems at the moment an event occurs.
- Mapping and validation against the chosen standard, with field-level rejects flagged early.
- Secure transmission through direct links or a third-party network, with automatic retries on failure.
- Receipt and parsing on the partner side, followed by immediate acknowledgments.
- Back-end integration that posts clean data into order-entry, accounts payable, or logistics systems.
Communication Choices and Their Trade-offs
Direct links promise lower latency, yet demand 24 × 7 monitoring. VANs simplify connectivity but charge per-kilobyte fees. Hybrid models split critical paths from low-value traffic. Whichever route you choose, insist on real-time visibility into message flow, or missed SLAs will surprise both finance and customer success.
EDI Message Standards and Industry Compliance
Standards give EDI its super-power: any two companies can exchange structured data without negotiating every field from scratch. The most EDI implementations, such as ANSI X12 in North America and UN/EDIFACT elsewhere, define thousands of transaction sets, each with a permanent reference number. X12 810 means invoice today and will still mean invoice in ten years. That stability is worth gold when your integration landscape spans suppliers, carriers, and government agencies.
Compliance is not only about syntax. Most industries layer business rules on top of the base EDI standard. A pharmacy claim must include a national drug code, while an automotive call-off demands a specific scheduling qualifier. Failing those rules triggers chargebacks or, worse, legal exposure. Mature EDI software validates each data element before release, preventing costly rework downstream.
Healthcare illustrates the point. HIPAA mandates specific transaction sets for claims (837) and remittances (835), plus audit trails that prove patient information never leaked. Aviation, energy, and public sector contracts come with similar rule books. An implementation guide may run to 300 pages, but following it means your messages clear customs or compliance checks the first time.
For leadership, the lesson is clear: standards compliance shields revenue. It turns integration from an artisanal effort into routine infrastructure, freeing engineers to focus on differentiating features rather than fighting formatting fires.
Implementation Realities: What It Takes to Deploy EDI Successfully
Implementing EDI is less about installing a server and more about aligning business processes, partners, and expectations. Many teams start because a flagship customer issues an ultimatum. The timeline is short, and penalties are real. The smartest move is to treat implementation as a program, not a ticket on the backlog.
Begin with EDI integration architecture. Will you bolt an EDI gateway onto the existing ERP, or insert middleware that handles mapping for multiple source systems? API-centric platforms now ship with pre-built adapters that translate REST payloads into EDI documents, a useful bridge when microservices drive the rest of your stack. Simpler organizations may lean on managed services where the provider owns both software and VAN connectivity.
Testing deserves its own budget line. Every partner has quirks that only surface under load. A pilot phase should include parallel runs, dual posting, and stress scenarios that mimic end-of-quarter peaks. Skipping this work saves money today and creates audit findings tomorrow.
Post-go-live support can make or break the ROI. Automated alerts must feed incident-response channels. Clear ownership prevents finger-pointing when an acknowledgment never arrives. Periodic map reviews catch field expansions and code-list changes before they break production.
Cost models vary. Per-document pricing looks harmless until volumes spike. Seat-based licenses favor lean teams but punish broad adoption. Leadership should ask detailed questions about storage fees, bandwidth tiers, and change-request charges. A transparent model lets finance compare in-house build, hosted software, and full managed service on equal footing.
In short, successful EDI programs balance technical rigor with practical governance. They treat mapping changes like code, enforce service-level metrics, and keep an eye on total cost as usage scales. When done well, the system becomes invisible—the best compliment any integration platform can receive.
Why EDI Still Powers Enterprise Scalability and Efficiency
Cost reduction used to be the headline benefit of Electronic Data Interchange, but resilience and scale have taken center stage. When order volumes double during a seasonal spike, an EDI infrastructure keeps pace without hiring data clerks or standing up extra call-center seats. Automated acknowledgments settle thousands of transactions per minute, preserving cash flow even when demand surprises the forecast.
EDI makes partner onboarding straightforward. Once a supplier agrees to the standardized format your integration team already supports, a new map and a certificate are often enough to start production traffic. That plug-and-play approach shortens time-to-revenue while keeping data quality intact. Leaders see the impact in shorter lead times, lower error rates, and faster month-end closes.
Finally, compliance teams appreciate the visibility that EDI provides. Each electronic transmission carries a timestamp, a digital signature, and an audit trail that satisfies both internal controls and external regulators. Instead of sampling paper based documents after the fact, finance and risk management review live dashboards that surface exceptions in real time.
Beyond the Basics: EDI as a Strategic Integration Layer
APIs and event streams have not replaced EDI, they have joined it. Forward-looking architecture treats EDI as one channel in a multi-modal integration fabric. Core transactional data still travels over secure protocols like AS2 or OFTP2, while analytics and customer-facing services read the same information through REST or gRPC. A well-designed middleware tier handles translation in both directions, turning EDI documents into JSON for microservices and, when necessary, feeding updates back into X12 or EDIFACT flows.
Cloud adoption accelerates this convergence. Managed EDI solutions now expose container-friendly endpoints and autoscale on peak days, yet they retain the compliance posture that legacy partners demand. The result is a hybrid model where reliability meets agility instead of blocking it.
Conclusion: EDI Remains a Pillar of Enterprise Operations
Software leaders chase innovation, yet they know stability funds the journey. EDI delivers that stability. It removes manual data entry, enforces contractual rules, and keeps business information flowing under tight service levels.
Until every trading partner worldwide agrees to abandon structured standards, EDI will remain the safest, fastest way to move high-value documents across company boundaries. Treat it as critical infrastructure, invest in modern tooling, and it will keep revenue moving while new technologies mature.
Frequently Asked Questions
How does “direct EDI” differ from using a third-party network?
Direct communication creates a point to point link between you and each business partner, giving you full control over certificates, retries, and monitoring. A value added network acts as an intermediary, simplifying connectivity at the cost of per-document fees and less granular visibility.
Do modern EDI solutions support API integration strategies?
Yes. Leading EDI systems expose REST and Simple Object Access Protocol (SOAP) endpoints that translate inbound API calls into EDI format and return functional acknowledgments. This lets cloud-native services consume validated data without speaking X12 or EDIFACT directly.
What role does a standardized format play in reducing errors?
A rigid, standard format forces every data element into a predefined location and length. That structure eliminates ambiguity, enables field-level validation, and prevents the downstream cleanup that plagues loosely structured files. Fewer errors mean faster reconciliation and lower operating cost.
When should we consider moving from an on-premise gateway to a cloud EDI platform?
Trigger points include increasing document volume, a need for global redundancy, or a mandate to retire aging hardware. Cloud EDI platforms handle burst traffic automatically and often bundle advanced analytics that on-premise gateways lack.
How can we measure the business impact of improved EDI transmission quality?
Track cycle time from purchase order to invoice acceptance, the percentage of EDI transactions that process without human intervention, and the dollar value of chargebacks avoided. Improvements in these metrics translate directly into working-capital gains and higher customer satisfaction.
Are there security concerns when transmitting EDI documents over the public internet?
Security rests on encryption and authentication, not the transport itself. AS2, SFTP, and OFTP2 use strong ciphers, digital certificates, and checksum validation to protect data in motion. Regular certificate rotation and continuous monitoring close the remaining gaps.