Another helpdesk ticket lands. Another user is locked out thanks to a forgotten password. That may sound insignificant, but taken in aggregate it can overwhelm your team.
An estimated 20–50% of helpdesk calls are password resets, costing $70 per reset on average. That adds up to millions lost annually in time, resources, and productivity. For platform and security leaders, the stakes go beyond cost. Compromised credentials remain the root cause of over 88% web app breaches.
Layering on multifactor authentication hasn’t solved the problem. Users fatigue. Attackers adapt. The stack gets harder to maintain. Passwordless authentication offers a cleaner login and a way to cut support costs, reduce breach risk, and build a system that scales. The returns show up in both the SOC 2 report and the IT budget.
What Are Passwordless Logins?
Passwordless logins are user authentication methods that use techniques like biometrics or hardware tokens instead of traditional passwords. They make credential theft nearly obsolete. They also offer fast, frictionless access in modern enterprises.
Passwordless authentication methods include:
- Facial recognition
- Fingerprint scans
- Security keys
- Authenticator app push notifications
- Magic link emails
- Device-bound passkeys
- Smart cards
- Adaptive authentication mechanisms
Most of these use public key cryptography to securely verify user identity, with the user’s device bearing the private key and no shared secrets. For example, a Dell Latitude laptop might use fingerprint scan tech for quick logins. An authenticator app like Microsoft Authenticator can also send a bump request for passwordless access.
This shift eliminates weak passwords and reduces support costs tied to password resets. It also creates a better user experience. Passwordless systems can give IT teams stronger choices for secure access.
Why Passwords Fail Modern Security
Every time you roll out new password rules, you’re chasing your own tail. Your users reuse old passwords and jot them on sticky notes. Meanwhile, phishing attacks slip right past your training efforts. Even with constant reminders to practice better password management, your team gets stuck dealing with breaches.
Weak passwords are an open door for attackers. Businesses lose time and revenue patching holes after every user’s account falls victim to credential theft. You might lock down your password combinations, but it’s whack-a-mole. Attackers adapt, launching credential-stuffing attacks that aim for the same user’s identity across dozens of services. Stolen passwords make up the bulk of modern security incidents.
Key Methods of Passwordless Authentication
A 2022 report from the FIDO Alliance showed that up to 80% of data breaches involved weak or stolen passwords. With credential theft still a leading risk, businesses want alternatives that boost user authentication without sacrificing experience. Here’s a clear view of today’s top passwordless authentication methods and the trade-offs behind each one.
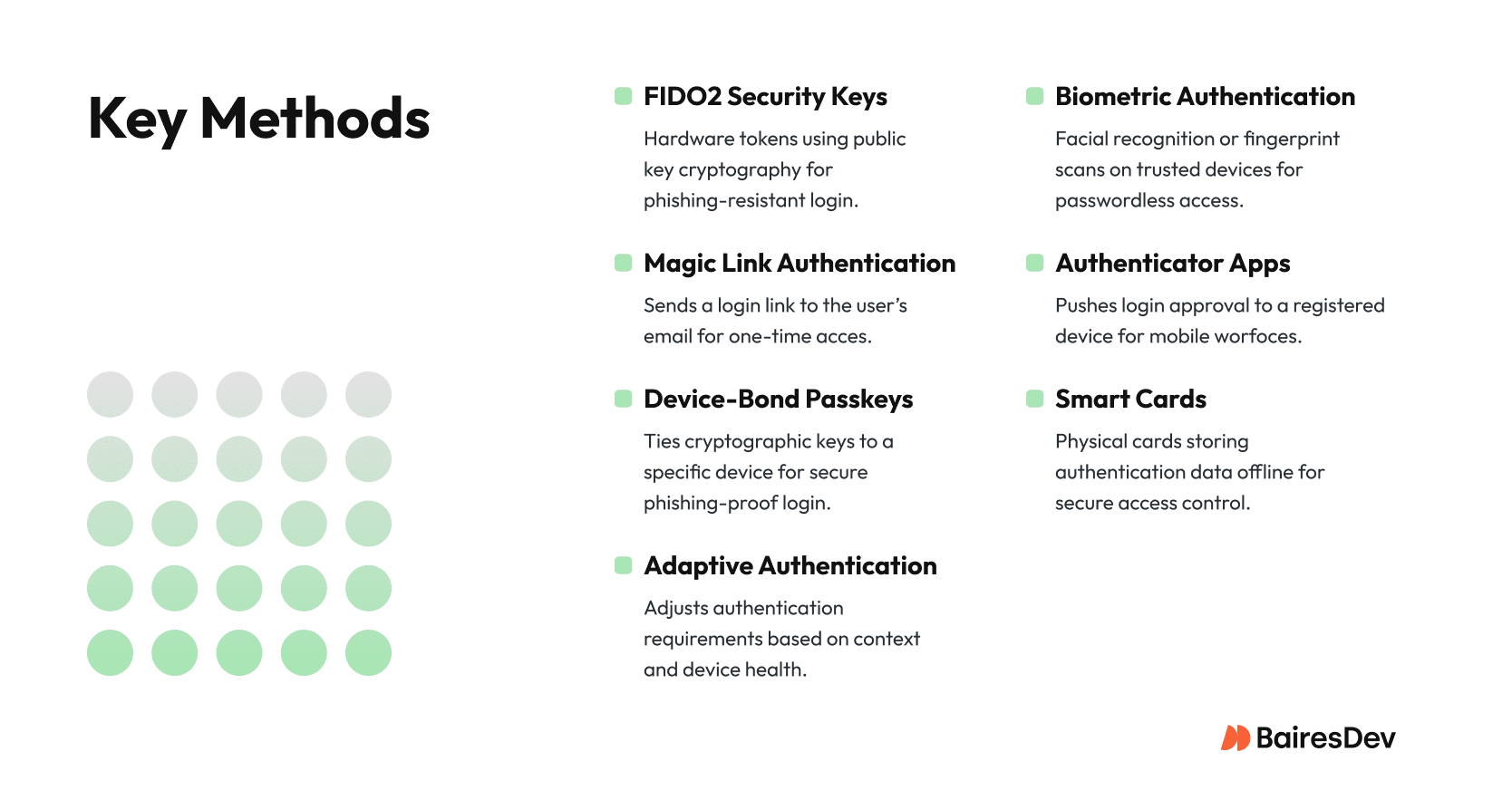
FIDO2 Security Keys (YubiKey 5 NFC, Titan)
Security keys are small USB or NFC devices that verify user identity using public keys. In standard implementations, the private key never leaves the device, so they’re highly resistant to phishing and credential theft. Compatible with FIDO2 and WebAuthn standards, they work across major platforms like Windows, macOS, and modern browsers.
They’re especially valuable for admins and high-security environments, where compromised credentials carry serious risk. At scale, successful deployment requires asset tracking, streamlined key issuance, and recovery processes to manage distribution and loss.
Biometric Authentication (Face ID, Windows Hello)
Biometric authentication leverages facial recognition or fingerprint scan on a user’s device. Only the user’s identity unlocks access. For example, iPhone with Face ID lets users tap-and-go instantly. Adoption hurdles include privacy and device compatibility.
These excel in mobile device fleets, and when seamless user experience is critical.
Magic Link Authentication
Magic link authentication sends a login link or code to the user’s email address. This login mechanism is easy to deploy and cuts down on forgotten passwords, but depends on secure email infrastructure.
It’s popular for short-term user access or customer portals where frictionless access trumps maximum resilience. Be warned that since it relies on email security, if the user’s email is compromised, the magic links become a weak link. Also, avoid reuse or replay of links.
Authenticator Apps
Authenticator apps like Microsoft Authenticator send a push notification to a registered device. It’s a go-to for workforce mobility. The bump request makes logins fast, but reliability depends on network access and user vigilance.
Authenticator apps suit hybrid and remote-first teams where the device variety is high. Note that these are often not strictly passwordless in the purest cryptographic sense. They typically still depend on a shared secret or token exchange, so they belong more to “strong MFA.”
Device-Bound Passkeys
Device-bound passkeys use public key cryptography to generate unique credentials, with the private key only on the user’s device. This offers phishing-proof login but requires careful onboarding and recovery planning.
Adoption is accelerating where secure authentication methods are part of zero trust architecture.
Smart Cards
Smart cards remain the gold standard in government or financial regulations. Hardware tokens work offline and can serve as a first authentication factor.
Use them for sensitive access management or where compliance leaves no room for risk.
Adaptive Authentication Mechanisms
Adaptive authentication factors blend context and device health to adjust login requirements on the fly. The result is a digital handshake that feels frictionless for users while keeping hackers out.
Implementation means tuning policies and investing in robust data stored analysis, but it offers smart defense for distributed organizations.
Protocols and Standards
Enterprises moving to passwordless authentication need to understand the protocols under the hood. FIDO2, WebAuthn, and OAuth2 extensions are the backbone. But compatibility isn’t guaranteed out of the box. Engineering teams must account for device support, browser behavior, and ecosystem alignment before selecting a preferred authentication method.
- FIDO2: Public key cryptography, no shared secrets, strong phishing resistance
- WebAuthn: W3C standard for browser and platform authentication APIs
- OAuth2 Extensions: Used for federated identity and layered security in complex environments
- Platform Requirements: Ensure OS, browser, and endpoint device compatibility
- Ecosystem Fit: Confirm identity provider support before adoption
Architecture Choices: Hosted vs Embedded Auth
Choosing between hosted and embedded authentication shapes how tightly auth integrates with your platform. Hosted services like Auth0 and Okta offer fast deployment, built-in compliance, and support for multi-factor authentication out of the box. But they can limit control, introduce vendor dependencies, and create challenges in aligning with custom login flows or platform-specific UX standards.
Embedded authentication gives teams full control over the login process and tighter integration with internal systems and existing IdPs. It demands more upfront engineering effort and ongoing maintenance, but it can simplify long-term consistency across platforms.
The right approach depends on whether your team is more focused on speed to market or architectural control. It also depends how you plan to scale and govern access as users gain access across systems.
Steps to Implementation
Your journey to frictionless authentication with passwordless methods starts with a clear plan and the right details. It’s no wonder Zero Trust Architecture has become the north star for IT leaders charting a passwordless journey. Here’s how to pull it off at scale.
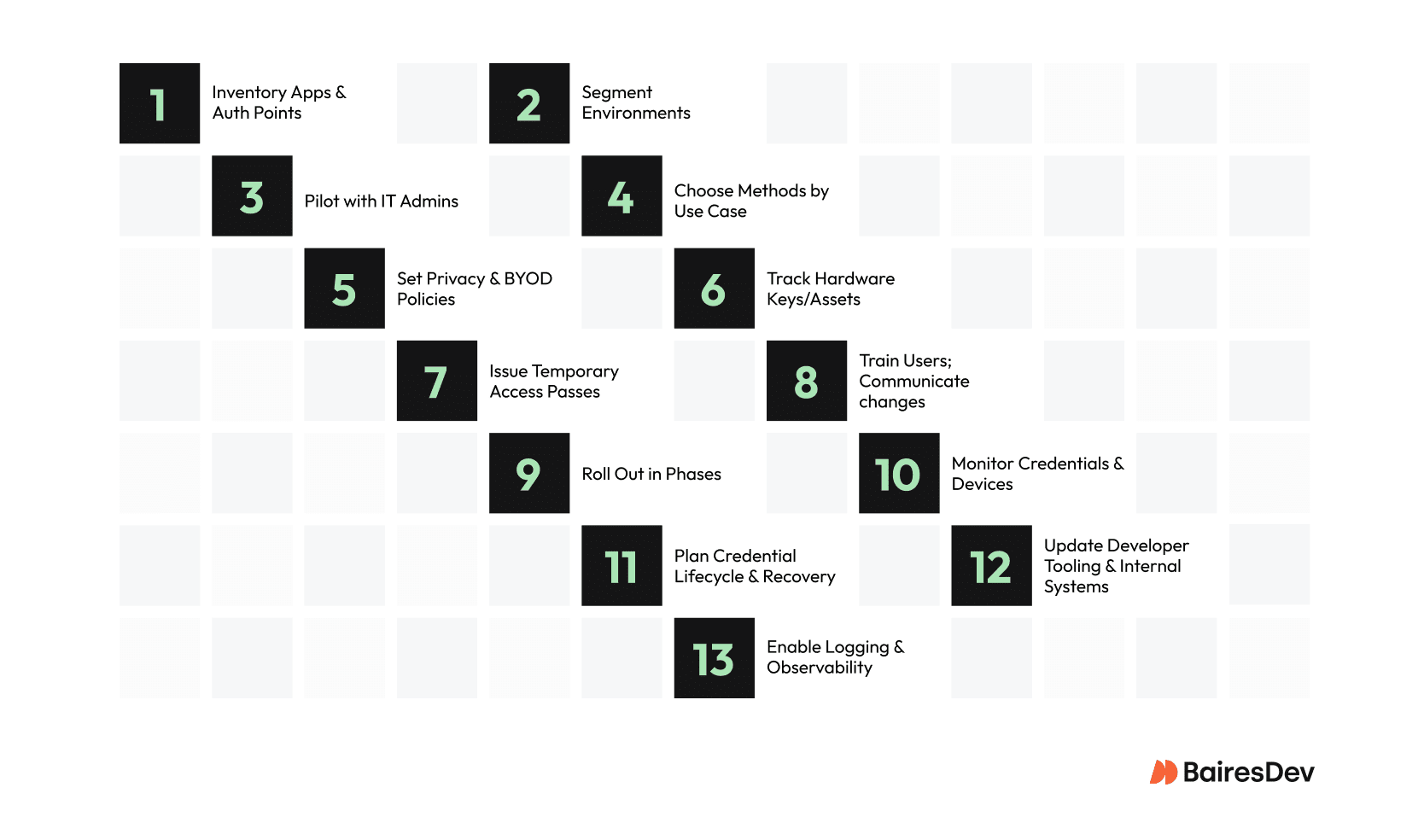
1. Inventory Applications and Authentication Protocols
Map every user account and authentication process. The idea here is to uncover outdated methods like workflows built on outdated tokens. This search will show you where you need upgrades or middleware. It’s also where you’ll plan credential lifecycles covering recovery and lost or stolen devices. Following this step sets you up for a consistent login process.
2. Segment Environments
Identify which platforms are cloud-native, hybrid, or still on-prem. This helps match authentication choices to environment needs and flags integration gaps early. Plan for middleware or phased rollout where needed. Don’t skip edge case testing. Shared machines, guest sessions, and device resets often reveal compatibility issues that standard test plans miss.
3. Pilot with IT Teams
Start with IT admins to test new authentication factors in a controlled setting. Early feedback helps refine flows and catch integration issues. It also surfaces how the system responds to failed recovery attempts and shared machines. These kinds of cases that don’t always show up in broader pilots but can derail the login flow if left unchecked.
4. Select Passwordless Methods by Use Case
Different environments call for different approaches. FIDO2 security keys suit regulated finance roles. Facial recognition works for field teams with managed devices. Magic links are useful for short-term or high-turnover roles. Tie each method to risk profile and workflow. Avoid shared secrets where possible.
5. Add Privacy Policies
You need policy-driven onboarding to manage asset issuance, set BYOD boundaries, and address privacy concerns. Clearly communicate what will change and who’s affected. Don’t overlook developer onboarding either. Passwordless steps should be part of their checklist to avoid delays accessing secured tools on day one.
6. Use Asset Tracking for Hardware (FIDO2 Keys, Smart Cards)
Track every security key in inventory to prevent loss and key clutter. Use a dashboard to manage provisioning and recovery. Good records simplify audits and reduce delays. This is also the point to validate fallback options like backup factors and account recovery steps. Documentation keeps a lost key from causing lost access.
7. Create Temporary Access Passes for First-Time Setups
Give first-time users a Temporary Access Pass that’s controlled, time-boxed, and limited in scope so no one is locked out before full registration. This eases onboarding and minimizes early support load. It also contains risk while the user’s private key is being established and linked to their identity.
8. Educate and Communicate
Train users to spot authenticator app prompts early in the rollout. Reinforce PIN hygiene and offer help channels for adoption. Brief teams on how to respond to high-volume or unexpected bump requests so approvals stay intentional, not automatic. Pay special attention to Google Authenticator requests. Clear guidance reduces risk and builds trust in the system.
9. Phase Rollouts
For every new phase, monitor for soft lockout and reset issues. Run scream tests on small groups to catch pain points quickly, refining your approach with real user attempts before scaling wider. Track numerical data like failure rates and fallback usage to validate changes and spot friction early. Each round should reduce surprises and make the next rollout smoother.
10. Monitor
Automate monitoring of active credentials, PIN hygiene, and device status. This helps detect issues early like stale keys or insecure PINs before they affect access. Logging should include failed login attempts and fallback usage to support audits and improve the process over time.
11. Credential Lifecycle Planning
Passwordless adoption isn’t complete without lifecycle controls. Plan for account recovery, lost or stolen devices, and backup factor provisioning from day one. Define fallback processes that minimize disruption without weakening the system. Automating recovery reduces support load and avoids delays when employees need to gain access quickly.
12. Developer Tooling and Internal Systems
Passwordless changes impact more than production auth flows. CI/CD pipelines, automation scripts, and bots often need alternatives, since most systems don’t support non-human logins. Internal dashboards and legacy apps may require adapters or code updates to support modern protocols. Developers also need local override modes or test credentials to simulate flows during development.
13. Auth Logging and Observability
When logins fail, engineers need visibility. Logging and traceability are essential to spot configuration issues, blocked factors, or attempted misuse. A strong observability layer makes debugging faster, strengthens compliance reporting, and reassures teams that passwordless authentication safe deployments remain predictable at scale.
Real-World Challenges and Tradeoffs
Passwordless doesn’t mean “easy for IT teams.” You could deploy the best passwordless authentication methods on offer, yet face hurdles every step.
Security is driven by people and tradeoffs. Operational speedbumps can make or break any rollout. These are the in-the-trenches challenges, with proven workarounds you’ll want in your toolkit.
| Challenge | Enterprise Impact | Common Workarounds |
| Legacy Systems (Kerberos, LDAP) | Prevents “rip and replace” upgrades | Integrate SSO wrappers, build middleware, use hybrid authentication |
| Device/PIN Complexity Gaps | Weakest link, unenforced PINs | Audit, require PIN hygiene |
| BYOD Resistance | Privacy, compliance | Offer “bring your own key,” communicate privacy |
| Hardware Key Management | Loss, theft, tracking admin pain | Asset tracking, self-service portals, enforce return policies |
| Hotel PCs / Shared Devices | TPM registration/user limits | Use FIDO2 in compatible “shared” mode |
| MFA Fatigue, Social Engineering | Accidental approvals, fatigue-driven risk | Education, adaptive authentication, use phishing-resistant factors like FIDO2 |
| Credential Recovery | Loss of keys disrupts access | Temporary Access Passes, backup devices |
| Credential Lifecycle Complexity | Inconsistent recovery options across auth types | Enforce backup enrollment, time-boxed access passes, automate reset flows |
| Developer Tooling Gaps | Internal systems may not support modern auth flows | Update internal SSO integrations, mock auth in test environments |
Adapting to Legacy and Hybrid Environments
A global firm manages cutting-edge cloud ERP and customer tools, yet still has teams logging in with the same password from ten years ago on a mainframe. Cloud-based apps benefit from passwordless authentication almost instantly. But legacy authentication systems such as LDAP or Kerberos slow the journey.
Device-based authentication shines in greenfield cloud projects. Phased adoption allows the security keys and authentication factors from modern systems to work alongside older authentication methods. Middleware adapters or SSO overlays can act as bridges supervising user identity and enabling passkeys for the same user across both new and old platforms. Over time, these adapters add operational complexity and cost. Long-term support and middleware lifecycle planning should be part of the initial architecture discussion.
Vendor maturity and ecosystem fit matter when working across hybrid stacks. The wrong choice can create fragmentation or add risk if the provider doesn’t support legacy protocols well. Adding passwordless on top of older systems can lock you into brittle integrations with limited upgrade paths.
Passwordless systems often require careful user journey mapping. This is where BairesDev strengths come into play. External partners simplify access management, design compliant rollout pathways, and integrate device-based authentication into both cloud-native and legacy stacks.
With HP EliteBook series on desks and blazers in conference rooms the job gets done. Passwordless authentication work must always reconcile new tech with stubborn legacy assets for secure access that meets compliance and business objectives.
Checklist: Readiness Questions for Passwordless Rollout
Use this as a pre-launch audit you or leadership can walk through:
| ✅ | Readiness Question | Notes / Considerations |
| ☐ | Do we have complete inventory of all apps and authentication touchpoints? | This includes legacy, internal, SaaS, APIs. |
| ☐ | Is our identity provider / IdP / auth platform compatible with FIDO2 / WebAuthn? | Check versions, libraries, protocol support. |
| ☐ | Do endpoints and devices (OS / browsers) support the required auth factors (TPM, biometric APIs, USB/NFC)? | Understand gaps (old machines, BYOD). |
| ☐ | What fallback / recovery flows will we support (backup keys, Temporary Access Pass, email, etc.)? | Plan for lost devices or failed hardware. |
| ☐ | Do we have a secure key issuance, tracking, and revocation process? | Asset inventory, tracking loss, user offboarding. |
| ☐ | How will we phase rollout (pilot groups, high-risk users, all users)? | Start small, observe issues, gradually expand. |
| ☐ | Do we have logging and observability for auth errors, fallback usage, and credential health? | For debugging, compliance, monitoring. |
| ☐ | How will we educate users and onboard them (training, communications, materials)? | Clarity on steps, expectations, support. |
| ☐ | Are internal systems, developer tooling, and bots ready to work without passwords? | CI/CD, service accounts, legacy APIs may need adaptation. |
| ☐ | What compliance, audit, or regulatory implications do we need to account for? | E.g. requirements around MFA, identity proofing, revocation windows. |
| ☐ | Do we have a feedback loop and measurement plan (error rates, fallback rates, support ticket volume)? | Use metrics to validate adoption and catch friction. |
| ☐ | Are we prepared for exceptions (shared devices, kiosk / guest terminals, offline access)? | Define policies for edge cases. |






