Selecting an application architecture is an operational commitment that shapes how fast a product ships, how safely it evolves, and how much it will cost to run over time. Leadership often frames the choice between microservices and monoliths as a spectrum rather than a binary switch because the right answer depends on scale, process maturity, and market ambition. This article breaks down both approaches for leaders who carry the budget and the operational risk.
Across dozens of platform audits, our teams observed the same pattern. A monolithic architecture helps new products reach users quickly, but monoliths entangle release schedules once code and headcount grow. Microservices promise independence and resilience, yet they tax organizations that lack strong observability, automation, and service ownership.
Understanding where each model excels helps leaders set realistic timelines, staffing plans, and compliance postures. Armed with that context, a technology organization can choose an architecture that moves in lock-step with product strategy rather than standing in its way.
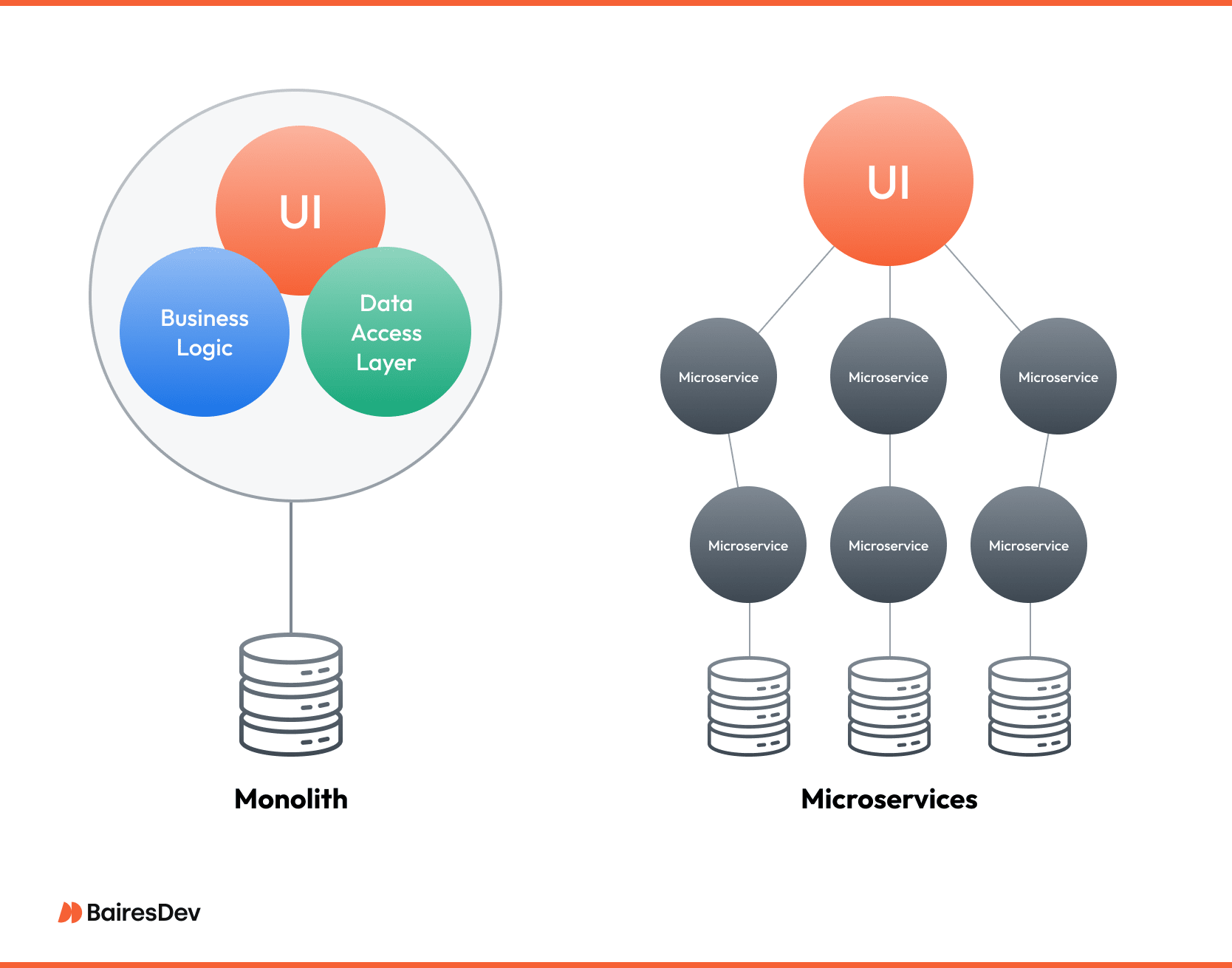
The Monolith: Simplicity That Scales, Until It Doesn’t
Under the traditional software development model, before distributed dashboards and service meshes, most enterprise stacks began life as one cohesive codebase. That single executable, the monolith, still solves plenty of real problems because it keeps everything in one place: business logic, data access, and presentation.
A straightforward deployment pipeline and a unified source of truth appeal to development teams that need rapid iteration without the cognitive overhead of coordinating multiple repositories.
When a Monolith Works
A monolith flourishes when product scope is limited and the team is small enough to share context informally. End-to-end transactions live inside one process, so latency is predictable and debugging usually starts with a single log file.
Schema migrations are less stressful because every module talks to the same database. In regulated environments where change windows are narrow, a monolithic application’s ability to roll back as a unit can be invaluable.
When a Monolith Fails
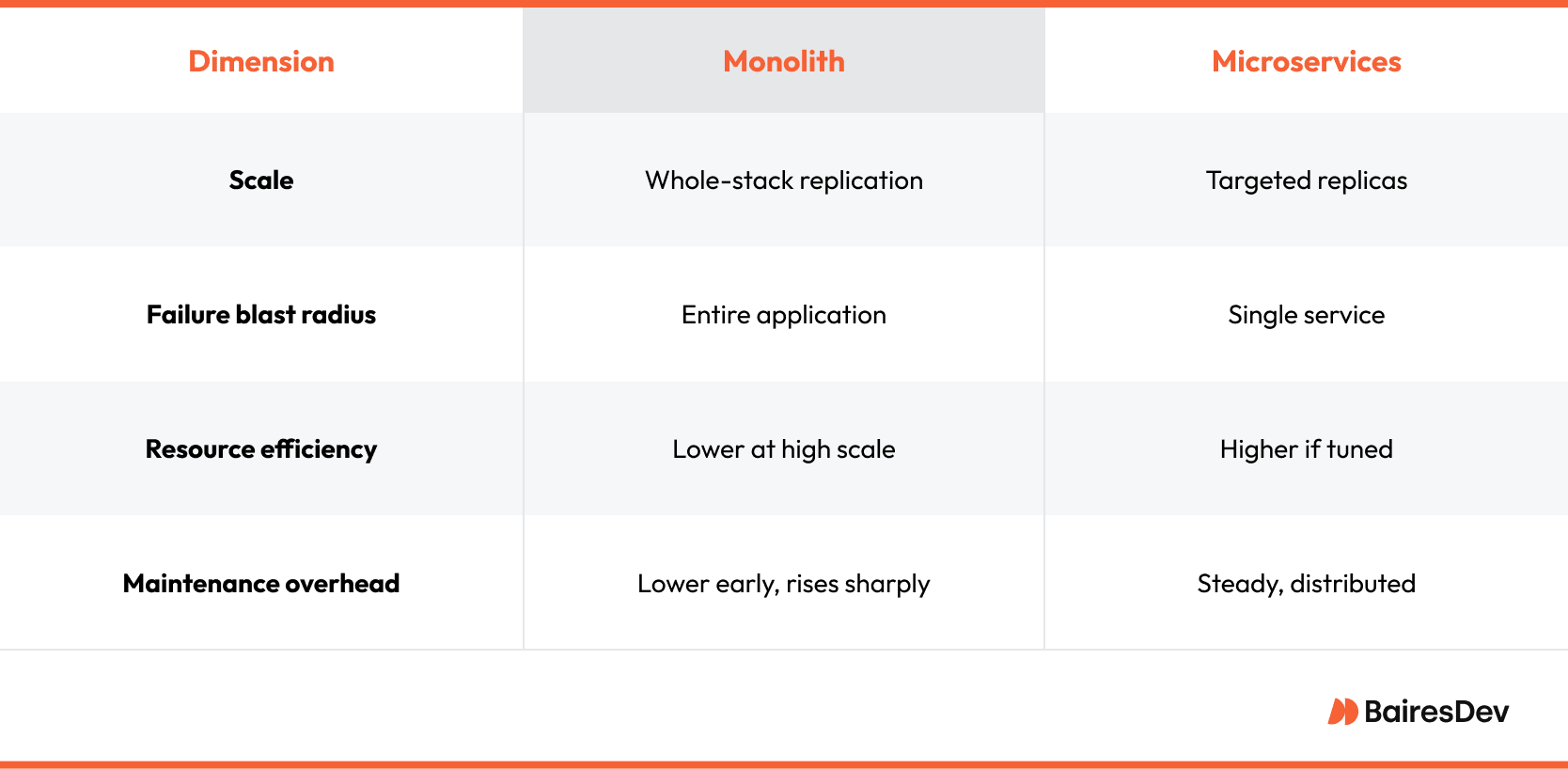
Trouble begins once the codebase grows beyond the memory of any one engineer. Release candidates wait in line because even a minor UI tweak triggers a full regression cycle. New hires must absorb the entire domain before pushing meaningful changes, slowing onboarding and diluting velocity.
As load increases, the only way to scale is to replicate the whole application stack, burning compute that might never be exercised and turning performance tuning into a high-stakes guessing game.
The hidden cost shows up in organizational dynamics. A single shared repository makes architectural ownership ambiguous, so every change request hops across fronts: product, QA teams, and operations. Over time, leaders notice that feature work competes with refactor tasks, yet both live behind the same deployment gate. The result is release anxiety that pushes teams toward either slower cadences or riskier weekend cutovers.
Neither option satisfies stakeholders who measure success in customer impact rather than deployment trivia.
The Microservices Approach: Flexibility, at a Cost
If the monolith is a single machine, microservices resemble a fleet. Each service owns one bounded context, lives in its own repository, and deploys on its own schedule.
Microservices applications gained traction because they decouples hot paths from cold ones and let engineering teams iterate without waiting for a global release train. That freedom, however, demands orchestration, observability, and intentional culture. Teams mush have a degree of microservices expertise.
Advantages of Microservices-based Architecture
A microservice can fail in isolation. In fact, multiple services can fail without dragging down the entire system.
The containment provided by microservices architecture is invaluable for customer-facing endpoints where downtime converts directly into churn. Horizontal scaling becomes surgical: replicas spin up only for components under stress, so cloud invoices better match traffic patterns.
Polyglot development is also back on the table. A search squad may reach for Go to optimize concurrency while a data squad leans on Python to ship a model, with no mandate to standardize prematurely.
Operational Complexity
Compared to a monolith architecture, the trade-off is operational surface area. Calls that once crossed a method boundary now hop across the network, bringing latency, retries, and partial failures. Observability moves from a single log file to a lattice of traces, metrics, and events that must converge on root cause quickly.
Without opinionated CI/CD pipelines, a modest schema change can set off a cascade of incompatible releases. Security fragments too. Every new endpoint is an attack vector and every secret becomes a distribution problem.
Cost of Change Shifts from Code to Organization
Technology is only half the story. Success correlates with team topology and ownership clarity. Service budgets, run-book maturity, and on-call rotations determine whether autonomy accelerates or slows delivery. Compute may drop thanks to targeted scaling, but the savings often reappear in observability platforms, message brokers, and incident tooling. Leaders who neglect that second ledger risk trading one bottleneck for an even pricier one.
An often overlooked dimension is data consistency. In a monolith, transactional integrity can rely on a single database. Microservices distribute data by necessity and must orchestrate state with patterns such as event sourcing or sagas. Those solutions work, yet they add queues, schemas, and replay semantics that the platform team must own indefinitely.
For regulated sectors like fintech or healthcare, or specific business functions, that extra surface demands rigorous audit trails and lineage tracking, which raises both operational overhead and compliance scope.
Comparing the Two: What Actually Matters
Architecture debates often stall on slogans, such as “monoliths don’t scale” or “microservices are too complex,” instead of the underlying forces. Development teams should evaluate four dimensions that show up on every executive scorecard: scalability, release velocity, organizational fit, and platform maturity.
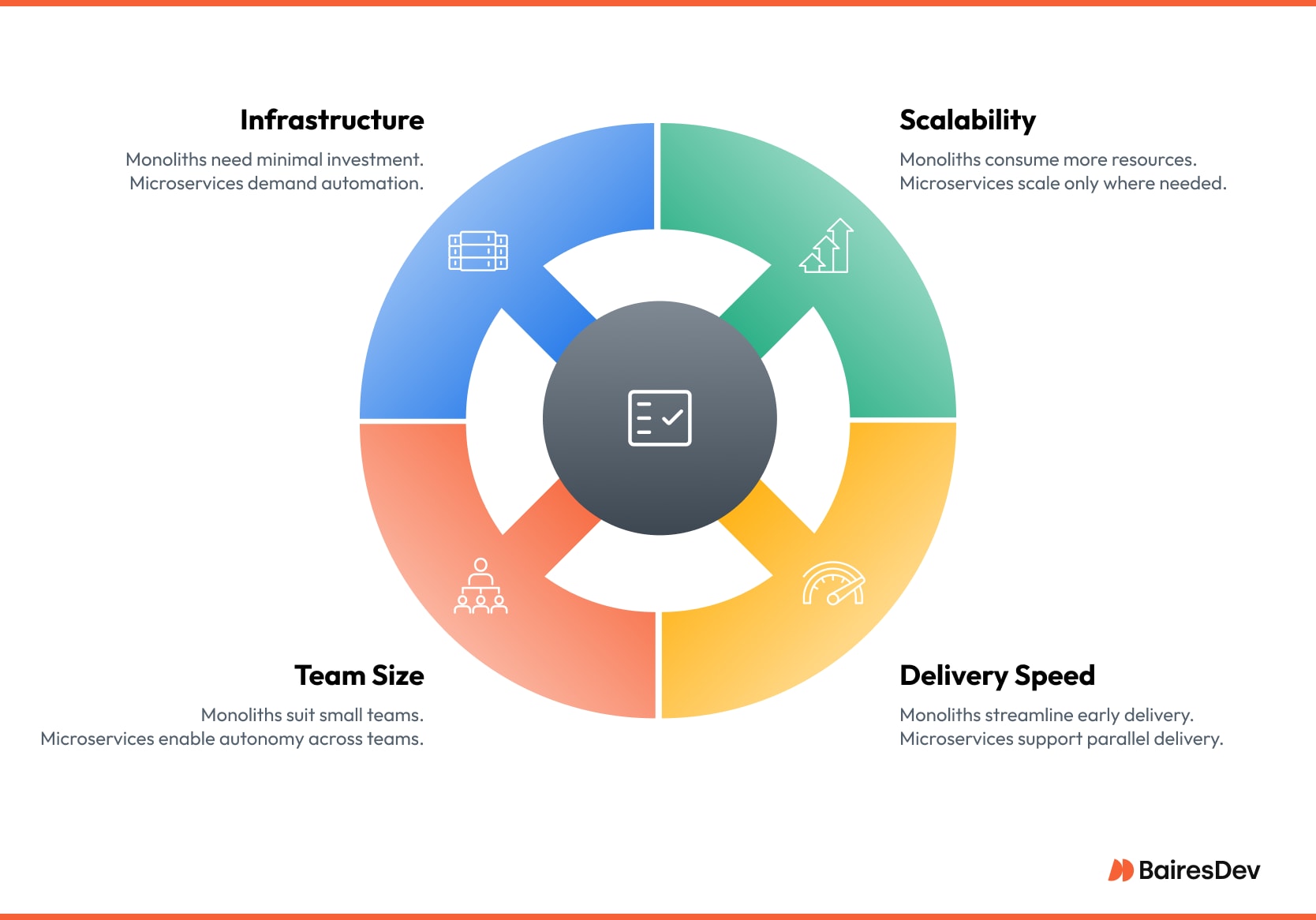
Scalability and Fault Isolation
A monolith scales by cloning the whole stack. That tactic is simple to automate, yet it multiplies resource consumption because idle components ride along with the busy ones. Outages follow the same pattern. A single memory leak can freeze the entire estate.
Microservices invert both constraints. Each service adds replicas only where demand is spiking, and a runaway process flames out locally instead of dragging the platform offline. The gap widens under sudden traffic bursts where targeted elasticity keeps user experience stable without over-provisioning the quiet zones.
Delivery Speed and Coordination Overhead
Speed is not just commit to production time. It is the sum of all hand-offs: code review, integration tests, compliance sign-off, and release windows. A monolith compresses those hand-offs because everything lands in one repository and one pipeline. As headcount climbs, that same pipeline becomes a choke point.
Microservices maintain pace by letting teams merge, test, and ship on independent rails, although every rail must still honor cross-service contracts. When those contracts break, mitigation work cuts into any time saved. Leaders weigh the savings from parallel delivery against the insurance cost of thorough integration testing and shared governance.
Team Size and Autonomy
Small groups thrive on shared context. A cohesive codebase reinforces that context, so junior developers spin up quickly and senior engineers can refactor entire workflows without coordination meetings. However, when the team reaches a certain size, or when multiple development teams become involved, the calculus flips. Context sharing becomes expensive.
Microservices let domain squads own code, data, and run-time. Autonomy, however, only delivers value when paired with accountability, clear SLAs, and a platform that shields teams from boilerplate concerns.
Infrastructure and Tooling Readiness
Executives often underestimate this axis. A monolith can live on a single CI server and a handful of dashboards. Microservices need pervasive automation: circuit breaking, distributed tracing, dynamic secrets, and service mesh policies.
Those systems cost money, but more importantly, they demand skill. If the platform team already runs Terraform pipelines, SRE on-call, and golden-path templates, the marginal burden of another service is modest. Without that backbone, every new microservice is an invitation to drift, toil, and late-night phonecalls.
When to Choose What: A Decision Framework
The question is not which architecture is “better” in the abstract. It is which one aligns with product ambition, budget tolerance, and organizational capacity.
When to Use a Monolithic Architecture
A monolithic architecture is the right fit when a product is young, its domain model is cohesive, and delivery needs to outrun market uncertainty.
Early releases benefit from one deployable artifact, straightforward rollback, and a single data store that enforces ACID guarantees.
Teams in heavily regulated sectors may also favor monoliths to limit audit scope. If the roadmap calls for quarterly feature drops rather than daily experiments, the monolithic cadence rarely feels restrictive.
When to Use Microservices
Microservices excel once revenue depends on continuous delivery, global uptime, and polyglot innovation.
Payment flows that cannot afford full-stack redeploys during peak hours, multi-tenant SaaS platforms, or other services facing unpredictable load curves all lean toward service decomposition. They unlock granular scaling, permit heterogeneous stacks, and isolate risk.
The catch is operational maturity. Leadership must budget for layered observability, automated dependency scanning, and product telemetry that feeds back into prioritization.
When to Use Both: Hybrid Patterns That Work
Some complex systems straddle both worlds. A modular monolith carves bounded contexts inside a single process, giving teams clear ownership while postponing the cost of network calls.
The Strangler Fig pattern lets engineers peel services away from a legacy core, protecting customer flow while modernizing piece by piece. Backend-for-frontend layers slim down mobile payloads without rewriting the entire estate. Each hybrid move should map to a concrete pressure point, for example release cadence or vendor lock-in, so that complexity grows only where it pays for itself.
A useful litmus test frames the decision around the cost of change. If adding a feature requires multiple teams to coordinate and blocks the release train, decomposition is overdue. If new features are delivered smoothly and incident rates are low, leadership gains little by fragmenting the stack purely for architectural fashion.
The Hidden Dependencies: Teams, Process, and Platform
Architecture lives downstream from organizational design. Platform audits often show that the most elegant code collapses when the surrounding people, process, and tooling are not equally mature.
In a monolithic system, engineering discipline revolves around a single pipeline. Central logging systems, feature flags, and schema migrations sit on one shared path, so platform debt is obvious and usually addressed early. Microservices distribute that responsibility across dozens of independently deployable services. Each adds its own build job, alert channel, and on-call rotation. Unless leadership enforces clear service boundaries, the overhead of coordination can erase any performance gains.
Process readiness is the first pressure test. Continuous integration (CI) must catch contract drift long before production, and release automation must promote individual components without manual checklists. The second test is cultural. Squads need true end-to-end ownership as a single loop.
Finally, platform tooling has to abstract the boilerplate. Golden-path templates, centralized policy enforcement, and a shared developer portal keep technology diversity from spiraling into entropy. When those three pillars align, microservices create robust, loosely coupled systems that tolerate failure. Without them, every deploy feels like a moonshot.
Conclusion: Architecture as Org Design
Choosing between monolithic and microservices architectures is ultimately a decision about how an organization creates, ships, and safeguards software.
A monolith rewards focus and rapid alignment, but it becomes fragile once the codebase outgrows a single mental model. Microservices unlock scaling and faster development cycles, provided the organization invests in automation, observability, and empowered teams.
In practice, many high-growth companies walk a hybrid path, preserving cohesive domains inside a modular monolith while carving off high-volatility features as independent services. When the structure of the code mirrors the structure of the teams and the cadence of the market, architecture stops being a bottleneck and becomes a competitive advantage.
Frequently Asked Questions
How should we handle business logic in microservices vs. a monolithic approach?
In a monolith, shared business logic sits in one codebase and is easy to refactor—until it grows. Microservices push logic into individual services aligned to business capabilities, reducing coupling but demanding strict interface contracts and versioning discipline.
What role does continuous deployment play in a cloud based microservices architecture
Continuous deployment is the safety net that lets distributed components evolve daily without human gates. Automated rollbacks, staged rollouts, and policy-as-code are essential when dozens of services deploy independently across multiple regions.
Can service oriented architecture help us untangle tightly coupled legacy systems?
Yes. SOA introduces coarse-grained services around domain concepts, creating seams that let teams extract functionality gradually. It reduces risk compared with a big-bang rewrite and offers a clear migration path toward finer-grained microservices later.
How do communication protocols and service boundaries affect improved fault isolation?
Protocol choice (gRPC, REST, messaging) governs latency and error semantics, while well-scoped boundaries limit blast radius. Together they enable fault isolation, letting one failing service degrade gracefully instead of cascading across the entire application.
When does it make sense to keep complex applications inside a modular monolith?
If workflows share heavy data access and real-time consistency, a modular monolith avoids the overhead of inter-service communication. Encapsulating modules behind clear interfaces preserves team autonomy while delaying the need for distributed systems tooling.
How can we add new business capabilities without disrupting existing user interfaces in a hybrid architecture?
A strangler-fig pattern works well. Route specific endpoints to new services while the legacy user interface continues to call the monolith. Gradual traffic shifting lets teams validate performance and reliability before a full cut-over.





