Today’s cyber landscape is unforgiving. Proactive application security testing, embedded within a rigorous software testing program, is now the first real line of defense.
By scrutinizing code, configurations, and runtime behavior before each release, engineering leaders convert invisible risks into actionable tasks: preserving revenue, reputation, and customer confidence.
Security Testing is Not Optional
Security testing has moved from optional hygiene to a board-mandated practice. Compliance frameworks such as SOC 2, ISO 27001, and HIPAA all require proof of secure development. When security testing is woven into every phase of the software development lifecycle (SDLC), teams can demonstrate the integrity, confidentiality, and non-repudiation controls regulators expect and customers demand.
The Rise of Security Threats
The urgency is unmistakable.
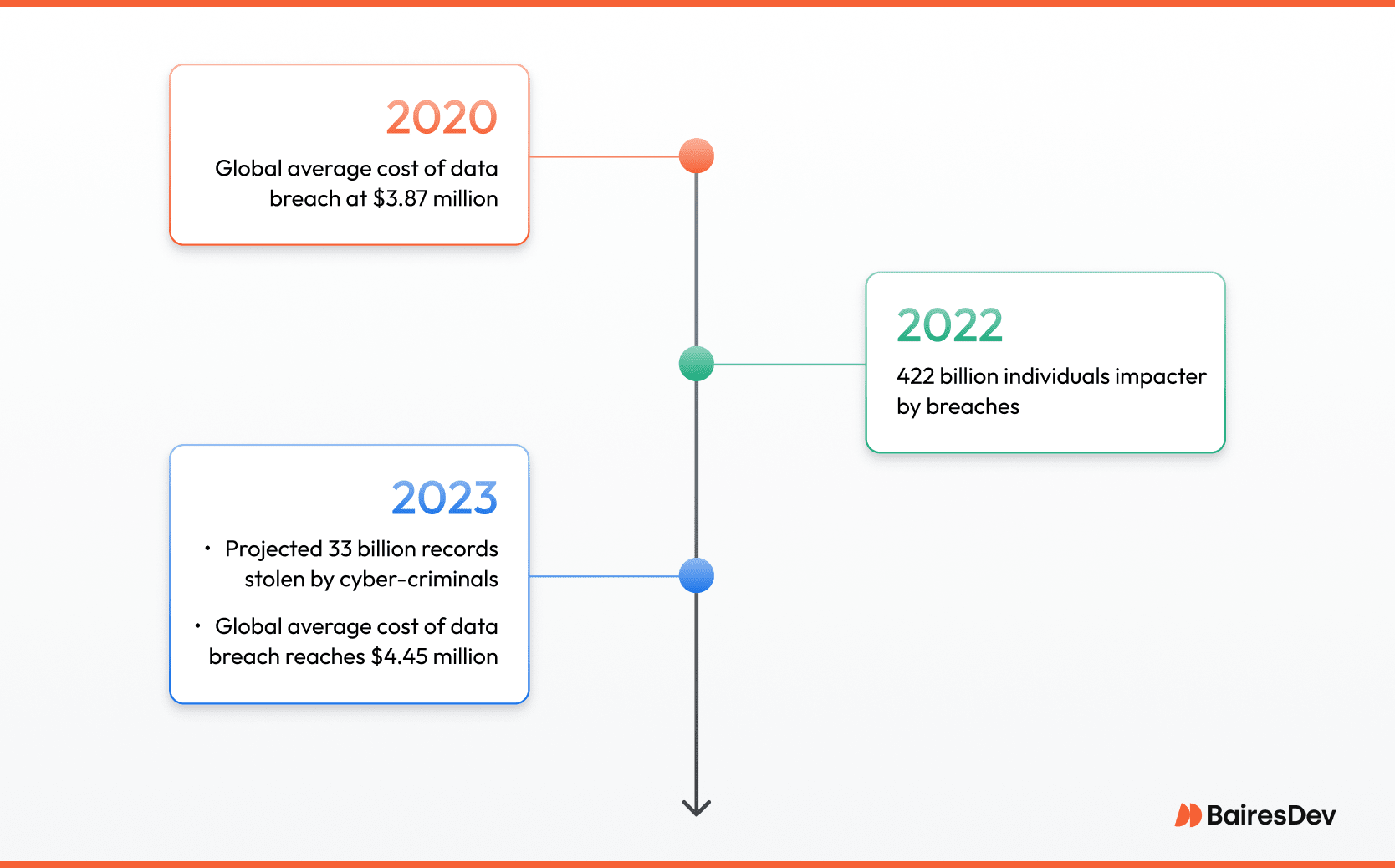
Analysts project cyber-criminals will have stolen more than 33 billion records during 2023, a 175 percent surge in just five years. According to Statista, in 2022, 422 million individuals felt the impact of breaches, leaks, or exposures. These figures translate directly into business risk: the global average cost of a data breach reached $4.45 million in 2023—up 15 percent since 2020.
Beyond direct attacks, insecure third-party components and hastily assembled supply-chain integrations amplify exposure. A disciplined security-testing regimen that inventories open-source libraries, scans containers, and validates infrastructure-as-code gives leadership a clear view of systemic risk across the portfolio.
Business Implications
Brand credibility erodes fast when customers read headlines about lost data. Forty-six percent of organizations report long-term damage—lost contracts, lower valuations, rising churn—after a breach. Once trust is broken, users rarely grant a second chance; they turn to competitors that can prove stronger safeguards.
The good news: integrating static and dynamic analysis, penetration exercises, and continuous monitoring into modern DevOps pipelines allows teams to surface issues early and remediate for pennies on the dollar compared with post-incident recovery, all without stalling release schedules. For enterprises operating in a zero-trust world, robust security testing inside a mature software testing strategy marks the difference between firefighting crises and confidently delivering innovation.
Types of Security Tests
Let’s go over the different security tests the industry relies on. Plain language, no jargon, no slides:
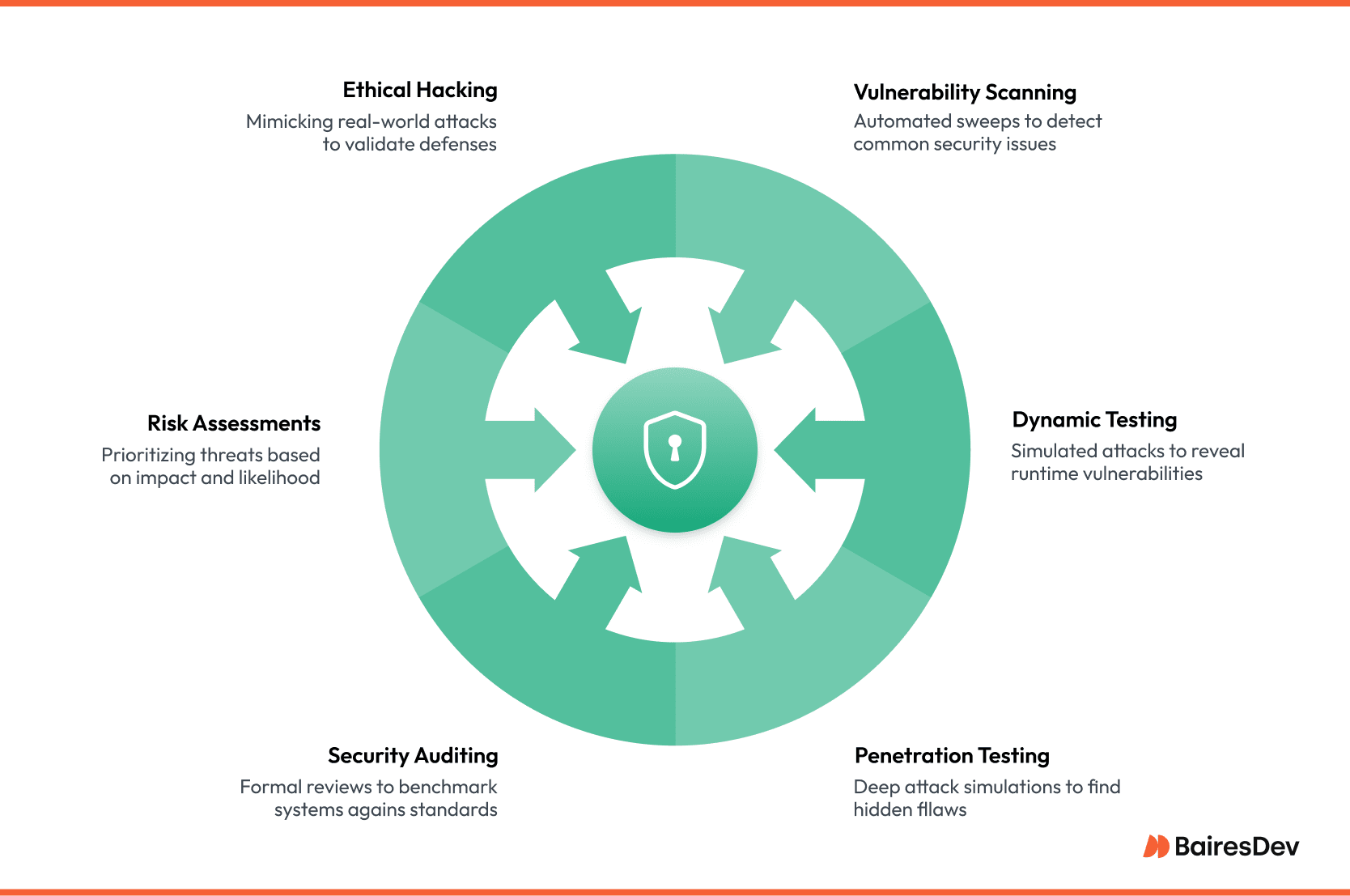
Vulnerability scanning
Picture an always-on sensor sweeping our network every night, looking for doors we forgot to lock: outdated libraries, weak passwords, mis-set permissions, and other security vulnerabilities. Tools like Nessus or Qualys generate a to-do list for teams before most of us have even poured coffee. It’s routine, almost mundane, yet it catches the “obvious stuff” attackers love to exploit.
Dynamic testing
Instead of poking at static code, we aim traffic at the running application, creating our own controlled attack. Think of it as a dress rehearsal: we fling malformed requests, see how the app responds, and note any place it stumbles. Because this runs in the pipeline right after every build, flaws show up hours before release.
Penetration testing is the heavyweight bout
Once a year (and after major launches), security teams invite red-team specialists to think like criminals and conduct penetration testing. In a black-box test they start cold, just a URL and their wits. White-box means they get the schematics, source code, even a chat with architects. Grey-box sits in between. The mix matters: it exposes both the outsider’s first strike and the insider misconfigurations automation never spots.
Security auditing
A security audit examines the complete system to assess how well in conforms to established security criteria. Auditors map the software against SOC 2 or ISO 27001 controls, interview staff, sample logs, and verify the team actually does what it claims. The auditor goes through a series of steps including risk assessment, testing system vulnerabilities, a review of security controls, and policy compliance evaluations to perform the most holistic view of a system’s entire security defenses. Security auditors utilize tools like Nmap and Wireshark.
Risk assessments
Risk assessments tie it all together. Rather than chase every vulnerability, risk assessment allows teams to rank issues by likelihood and business impact. This assessment examines many elements, including the possible impact of threats, the likelihood of an occurrence, and the potential vulnerabilities. A flaw on a demo site is a mosquito bite; the same flaw on production payments is a heart attack. Frameworks like Microsoft’s Threat Modeling help teams decide where to spend each security dollar.
Ethical hacking
Using their skills for good and not evil, ethical hackers simulate cyberattacks to expose system vulnerabilities before the real cyber criminals do. Mimicking real-world attacks, they validate defenses, stress incident-response runbooks, and provide an accurate assessment of an organization’s security posture.
Layered together, these practices transform security from a quarterly scramble into a continuous, measurable discipline, and they let security specialists walk into stakeholder meetings knowing they can back every claim with evidence.
Open-Source and Targeted Utilities
For teams that value transparency and rapid iteration, the open-source ecosystem delivers a rich toolbox.
OWASP ZAP, the community’s flagship proxy, pairs passive inspection with active attack simulations and can crawl modern single-page apps through its AJAX spider.
Wapiti extends coverage by hunting for cross-site scripting, SQL injections, and file-disclosure flaws across REST endpoints.
SQLMap is used when a more surgical approach is needed. This command-line workhorse automates every phase of an SQL-injection exploit—from fingerprinting the back-end engine to extracting sensitive rows—turning a tedious manual task into a repeatable check.
Burp Suite straddles the line between open and paid tiers, but even its free intercepting proxy earns a spot in most testers’ kits. By letting engineers tamper with live requests, replay attacks, and chain exploits, Burp exposes logic errors that scanners routinely miss.
Together, these security tools offer rapid feedback loops, deep protocol insight, and source availability for teams that audit their own security stack.
Enterprise-Grade Commercial Platforms
When the mandate is portfolio-wide coverage and governance at scale, commercial platforms step in.
Veracode combines static, dynamic, and software-composition analyses behind a single dashboard, flagging outdated libraries as readily as it tracks tainted data flows through complex microservices.
Nessus, meanwhile, serves as a network sentry; its continually updated plug-ins surface misconfigurations, missing patches, and lateral-movement paths an attacker might exploit.
Both vendors back their engines with compliance reporting that satisfies auditors and offers leadership a clear risk delta after each remediation sprint.
Making the Call
Tool choice should flow from threat model, application architecture, and talent bandwidth, not marketing checklists. Lightweight scanners excel during early sprints or for narrowly scoped APIs; full-stack platforms earn their keep when dozens of teams ship weekly and executives need a risk score before the quarterly board meeting.
The most effective programs blend the two: community utilities for rapid, developer-led feedback, and enterprise suites for governance, metrics, and scale. The result is a layered, cost-effective defense that keeps pace with both innovation cycles and evolving threats.
Security Tests: Best Practices
The best practices for security tests facilitate a more robust defense strategy while enhancing software resilience and limiting security risks. Development teams play a crucial role in integrating these security practices into the software development lifecycle.
Regular Testing
Dev teams must regularly perform security testing, integrating the practice throughout the development process and the software development life cycle, starting from very early on in development. Integrating routine security tests within the software development lifecycle (SDLC) as part of a DevSecOps approach is crucial. This fosters a more proactive defense strategy and identifies vulnerabilities sooner to better mitigate potential risks.
Keeping Track of the Threat Landscape
To effectively protect against cyber threats, companies must know what they’re up against by staying on top of the ever-evolving threat landscape. Resources like cybersecurity blogs and the National Vulnerability Database help testers and companies stay informed about the most recent vulnerabilities and known vulnerabilities to remain proactive in testing and fortification.
Collaboration Between Teams
Development, operations, and security teams must work collaboratively to amplify security protocol effectiveness. Security professionals play a crucial role in enhancing development processes through frameworks like DevSecOps. Based on this approach, DevSecOps development integrates security principles from the start of a project, incorporates regular code reviews, and fosters a culture of shared responsibility across teams while enabling quicker responses to threats.
Use of Automated Tools
Security scanning in security testing boosts the effectiveness and efficiency of the tests. Many tools exist to seamlessly identify and mitigate vulnerabilities automatically to foster a more fortified, resilient defense system.
Security Test Challenges
Security testing creates intricate challenges paired with a rapidly evolving realm of threats and complex architectures in computing systems. Dev teams must strive to stay ahead by taking a meticulous, adaptive approach to protocols while staying on top of the evolving threat landscape.
Evolving Cyber Threats
With new threats popping up regularly, testers face significant challenges in the ever-changing digital realm if they don’t maintain constant vigilance in monitoring new threats. Identifying potential security breaches is crucial as new vulnerabilities are constantly emerging in the realm of enterprise applications, necessitating frequent testing and regular updates to security measures. Recent examples of new threats include the ransomware attack on Colonial Pipeline and the SolarWinds hacking attack.
Limitations of Automated Tools
Automated tools can’t discern every potential vulnerability. Manual testing, including authentication testing, should complement any automated testing strategy. This ensures a more advanced and thorough approach to security assessments.
Resource Constraints
Due to budgetary constraints, companies frequently struggle to allocate sufficient resources for security testing. However, they must focus on utilizing the most cost-effective and robust security measures early on in the development lifecycle to produce more secure software and protect against threats.
Conclusion
As cyber threats continually escalate in frequency and evolve in complexity, companies must utilize a dynamic, multi-faceted defensive strategy or fall victim to an attack. Important factors include choosing the right tools for their needs, fostering collaboration across teams, and incorporating real-time testing and updates into their development lifecycle to improve the organization’s security posture.
An informed, proactive approach to security helps save companies enormous amounts of money, time, and reputational costs while fostering more user trust and safeguarding sensitive assets.
FAQ
What is the difference between penetration testing and vulnerability scanning?
Penetration tests, including automated vulnerability scans, identify and report system weaknesses based on predefined criteria, while penetration testing simulates cyberattacks to identify exploitable vulnerabilities.
Why is manual testing still important in security testing?
Manual testing is a vital aspect of security testing because it offers a nuanced, human-based analysis of things that automated tools have the potential to miss. The human touch discerns context-dependent, complex vulnerabilities to complement automated strategies, and code review plays a crucial role in evaluating software applications for such vulnerabilities. Together, these approaches create a more comprehensive security testing strategy.
How often should security tests be conducted?
Companies should conduct regular security testing to identify and mitigate security flaws, with a frequency determined by the software’s nature, the sensitivity of the data, and the user base.
Are there certifications for security testers?
Yes, certifications like the Certified Ethical Hacker and Certified Information Systems Security Professional enhance the expertise of security testers while validating their knowledge of security practices.
What is the role of AI and machine learning in security tests?
AI and ML enhance security testing tools with the ability to use predictive analytics and pattern recognition to identify and mitigate vulnerabilities with adaptive testing methodologies. Runtime application self-protection (RASP) further strengthens these tools by embedding controls within applications to monitor their behavior and defend against real-time security threats.






